What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

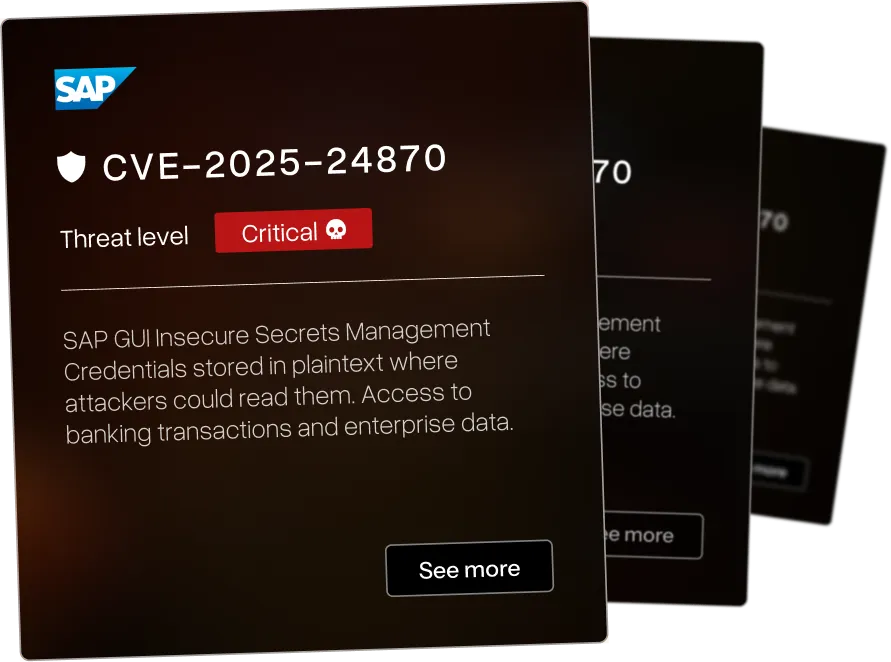
Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


Authenticated directory traversal and local file inclusion in Observium via different parameter






Authenticated directory traversal and local file inclusion in Observium allows reading server files






SQL injection in Observium via different injection point allows database attacks






Cross-site scripting in Observium network monitoring platform allows script injection






SQL injection in Observium network monitoring platform allows database manipulation






Cross-site scripting in SilverStripe Advanced Reports Module allows script injection






Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content






DLL hijacking in touchpad driver allows local attackers to execute arbitrary code with elevated privileges




.webp)

Insecure direct object reference in ACF to REST API WordPress plugin allows unauthorized data access via permalink manipulation




.webp)

Unauthenticated server-side request forgery in Bitrix CRM allows attackers to access internal systems




.webp)

Cross-site scripting with WAF bypass in Bitrix CRM allows script injection despite security controls






Remote command execution via unrestricted file upload in ExpressionEngine allows arbitrary code execution




.svg.webp)

Directory traversal in Apache Wicket allows reading Wicket markup source files from the server






Remote stored XSS via attachment name in Afterlogic WebMail Pro 8.3.11 allows persistent script injection






Arbitrary file upload leading to remote code execution in Energy Logserver allows server compromise




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.