TLPT DORA
for Financial Institutions
DORA-Compliant Threat-Led Penetration Testing by researchers who've published 150+ CVEs and tested financial institutions for 10 years
TLPT That Satisfies DORA
We deliver TLPT DORA-compliant testing aligned with Article 26 and TIBER-EU:
Threat Intelligence of Current Threat Scenarios
Red Team Testing of Assumed Breach Paths
Purple Team Exercises with Real-time SOC Collaboration
Remediation Validation of Security Fixes
We show you what breaks, how it breaks, and what customer data is exposed
We simulate threat actors who've breached your perimeter. We test if they can reach payment rails, manipulate SWIFT transactions, or compromise core banking. TLPT DORA shows which attack paths work and whether your defenses stop them.
Why Financial Institutions Choose AFINE for TLPT DORA
We've tested ING Bank, PKO BP, and other major European financial institutions in production for 10 years. You get red team operators who understand how threat actors move from breach to SWIFT access, payment manipulation, and core banking compromise. Our reports show exactly which controls failed, complete attack chains, and whether your SOC detected us.

Our Services
Threat Intelligence and Scenario Development
We analyze real-world threat actors targeting financial institutions. SWIFT compromise techniques, payment fraud methods, ransomware campaigns, and insider threats. We develop attack scenarios based on actual threats to your sector.

Core Banking and Payment Systems
We test core banking platforms, SWIFT messaging, payment processing, wire transfer authorization, and real-time payment rails. Testing if attackers can manipulate transactions or disrupt payment processing and whether your team detects it.

Digital Banking Platforms
We test online banking, mobile banking, and APIs connecting digital channels to core systems. Account compromise, session hijacking, transaction manipulation, and fraud detection bypass under realistic attack conditions.

Treasury and Back-Office Systems
We test financial reporting platforms, reconciliation systems, and payment approval workflows. Testing if attackers can move from back-office compromise to wire transfer capability and whether your controls stop them.

Third-Party Integration Security
We assess payment processors, fintech partners, correspondent banks, and SWIFT network connections. Testing if compromises propagate through financial supply chain relationships and whether your monitoring catches it.

Incident Response and Blue Team Assessment
We test your team's response to attacks they don't know are happening. Response activation speed, communication effectiveness during breaches, and recovery capability after compromise.

SOC Detection for Financial Threats
We test if your SOC catches credential theft from treasury operations, unauthorized SWIFT access, and wire transfer fraud before settlement. Real-world testing of detection capabilities.

Remediation Validation and Compliance Reporting
We present findings to your white team and stakeholders. Detailed vulnerability analysis, response effectiveness assessment, and remediation recommendations. Evidence formatted for DORA Article 26 compliance.

The Enterprise Security Software We Hacked
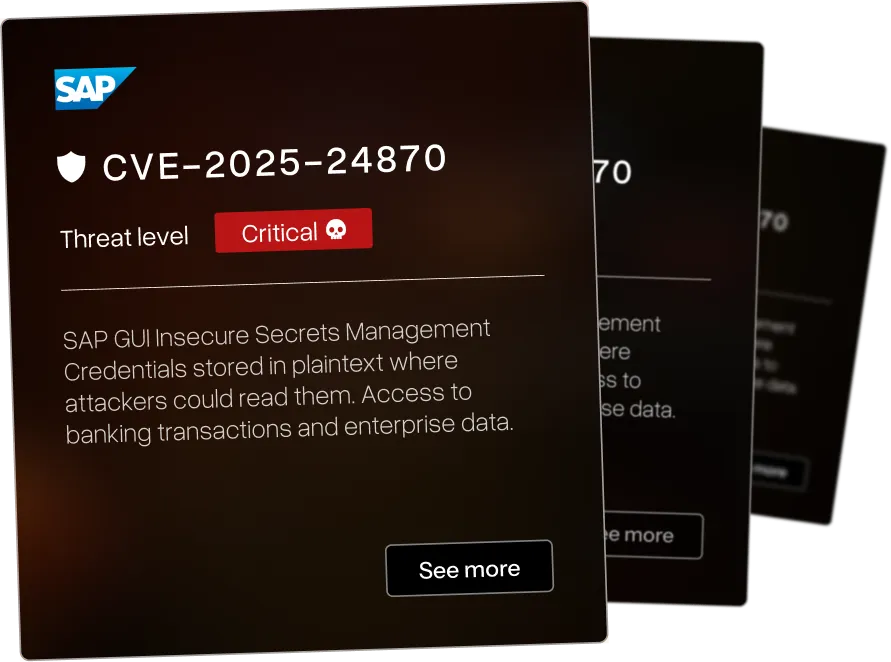
Our TLPT DORA researchers discover vulnerabilities in enterprise platforms running critical operations across banking and finance. We exploit both known CVEs and the vulnerabilities nobody's documented yet.


Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code






Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts




View All CVEs We've Published
.webp)


.webp)
The AFINE Adaptive Security Framework (AASF)
A framework developed from a decade of security assessments and continuously refined as attack methods evolve. Our methodology reflects current threat patterns and the practical security decisions organizations face as their attack surface expands.
We’re ready to deliver next-level security
Why Organizations Trust Us
TLPT DORA FAQ
Let's Discuss Your Security Posture
We scope every TLPT DORA engagement based on your systems and threats. Book a free assessment below to discuss your requirements.