What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


F5 BIG-IP Configuration Utility - Reflected Content Injection






TCC bypass via misconfigured Node fuses in Cursor AI code editor allows unauthorized access to protected macOS resources






Privilege escalation via get-task-allow entitlement in Invoice Ninja allows attackers to debug and manipulate the application process on macOS





TCC bypass via inherited permissions in bundled Python interpreter in GIMP.app allows scripts to access protected resources






Privilege escalation via get-task-allow entitlement in MacVim allows attackers to debug and inject code into the application process






Incorrect authorization of XPC Service in Fantastical.app allows unauthorized inter-process communication leading to privilege escalation




.webp)

Local Privilege Escalation due to world-writeable permissions in Adobe ColdFusion






TCC bypass via dylib injection in Postbox email client allows malicious code to access protected macOS resources




.webp)

TCC bypass via misconfigured Electron Node fuses in Nozbe allows malicious apps to access protected resources like camera, microphone, and files






TCC bypass via misconfigured Node fuses in Mosh-Pro allows applications to access protected user data without explicit consent






TCC bypass via dylib injection in Phoenix Code editor allows unauthorized access to protected user data on macOS




.webp)

Stored cross-site scripting in Rapid7 AppSpider Pro allows authenticated attackers to inject persistent malicious scripts






TCC bypass via dylib loading in Viscosity VPN client allows malicious code to access protected macOS resources






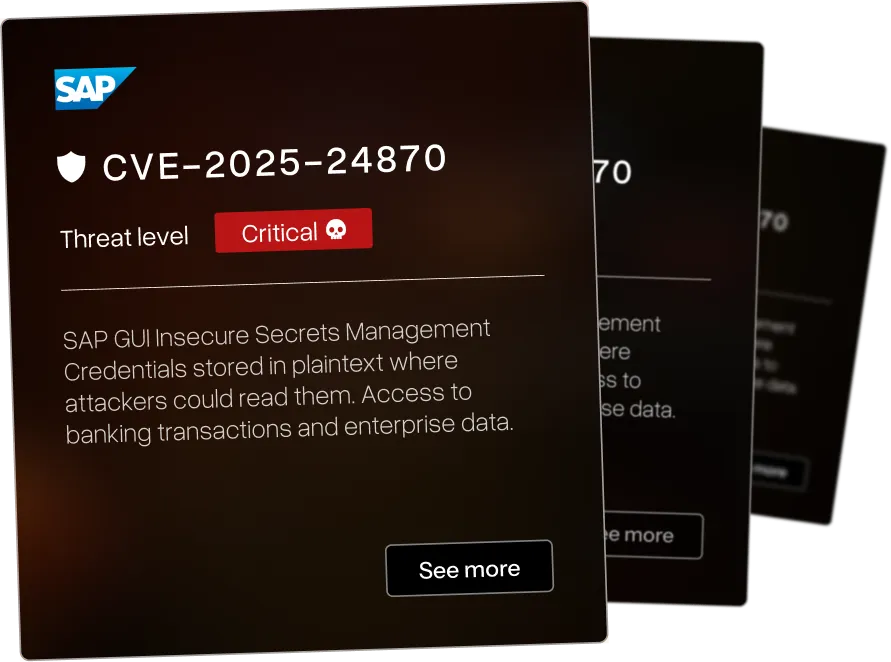
Insecure key and secret management in SAP GUI stores sensitive credentials in recoverable format, allowing local attackers to obtain passwords






HTML Injection vulnerability in SAP NetWeaver Application Server ABAP allows attackers to inject malicious HTML content into web pages viewed by other users




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.