What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


TCC bypass via dylib substitution in DaVinci Resolve allows malicious applications to access protected system resources






Connection pool exhaustion in Hackney HTTP client library allows remote attackers to cause denial of service




.webp)

Broken access control in Rapid7 AppSpider Pro < 7.5.021 allows standard users to place configuration files in directories belonging to other users/projects, potentially overriding security settings






Cross-site scripting in SAP NetWeaver Application Server ABAP allows injection of malicious scripts into web interfaces






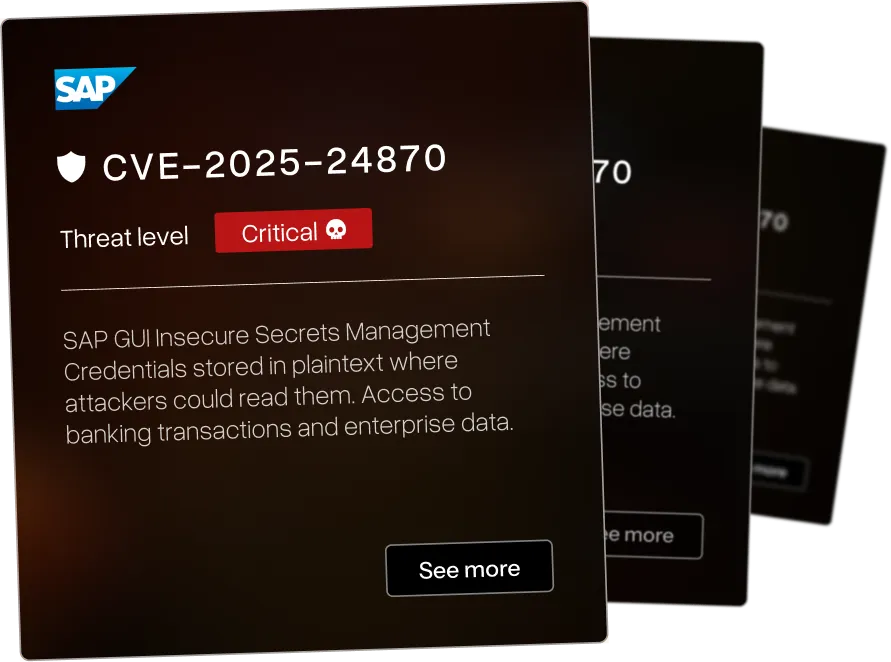
Insecure key and secret management in SAP GUI stores encryption keys in recoverable format allowing credential theft






HTML injection in CyberArk Endpoint Privilege Manager allows attackers to inject arbitrary HTML content






Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts






Self-reflected XSS in CyberArk Endpoint Privilege Manager allows script execution via crafted requests






IP spoofing vulnerability in CyberArk Endpoint Privilege Manager allows attackers to bypass IP-based access controls






Stored cross-site scripting in CyberArk Endpoint Privilege Manager allows persistent script injection in management console





Local privilege escalation in Atlassian Sourcetree for Mac allows local attackers to execute arbitrary code with elevated privileges






Dylib hijacking in Fast CAD Reader allows local attackers to execute arbitrary code by placing malicious libraries






Cross-site scripting in Ready_ Symfonia eDokumenty document management system allows injection of malicious scripts






Local file inclusion in Ready_ Symfonia eDokumenty allows attackers to read arbitrary files from the server filesystem






SQL injection in Ready_ Symfonia eDokumenty allows attackers to execute arbitrary SQL queries against the backend database




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.