What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
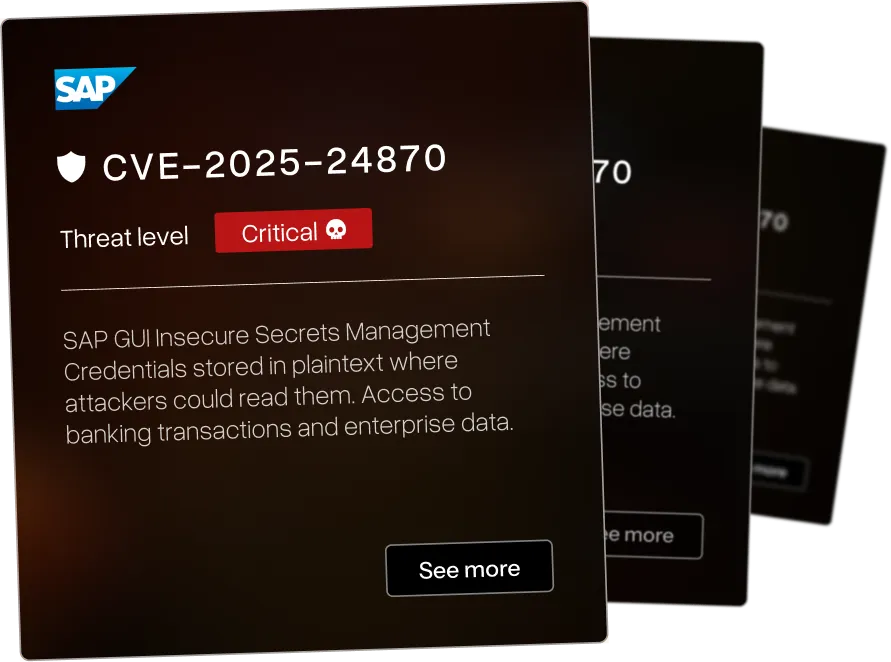
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


Remote code execution in Ready_ Symfonia eDokumenty allows unauthenticated attackers to execute arbitrary commands on the server





Remote code execution via CSV injection in Proget Console - activation data containing malicious formulas executes when opened in Excel





Stored XSS via unsanitized activation messages in Proget Console allows attackers to execute JavaScript in victim browsers





Stored cross-site scripting in Proget Console comments allows high-privileged users to inject malicious scripts affecting other administrators





Authorization bypass in Proget MDM allows low-privileged users to access MDM profiles revealing allowed and blocked device features





Insecure direct object reference in Proget MDM allows low-privileged users to view sensitive backup data including UUIDs, names, and emails





Authorization bypass in Proget MDM allows low-privileged users to retrieve device passwords using UUIDs obtained from other vulnerabilities





Broken access control in Proget MDM allows low-privileged users to enumerate task and device details including UUIDs via brute-force






Dylib hijacking in DaVinci Resolve allows local attackers to execute arbitrary code with application privileges






Local privilege escalation vulnerability in Sparkle autoupdate daemon allows local attackers to elevate privileges to root on macOS systems






TCC (Transparency, Consent, Control) bypass via Downloader XPC Service in Sparkle framework allows malicious apps to access protected user data without consent on macOS






HTML injection in AdmirorFrames Joomla extension allows attackers to inject arbitrary HTML content






Server-side request forgery in AdmirorFrames Joomla extension allows attackers to make requests to internal systems






Full path disclosure in AdmirorFrames Joomla extension reveals server filesystem paths to attackers






Cross-site scripting in Check Point Mobile Access portal File Share application allows injection of malicious scripts




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.