What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
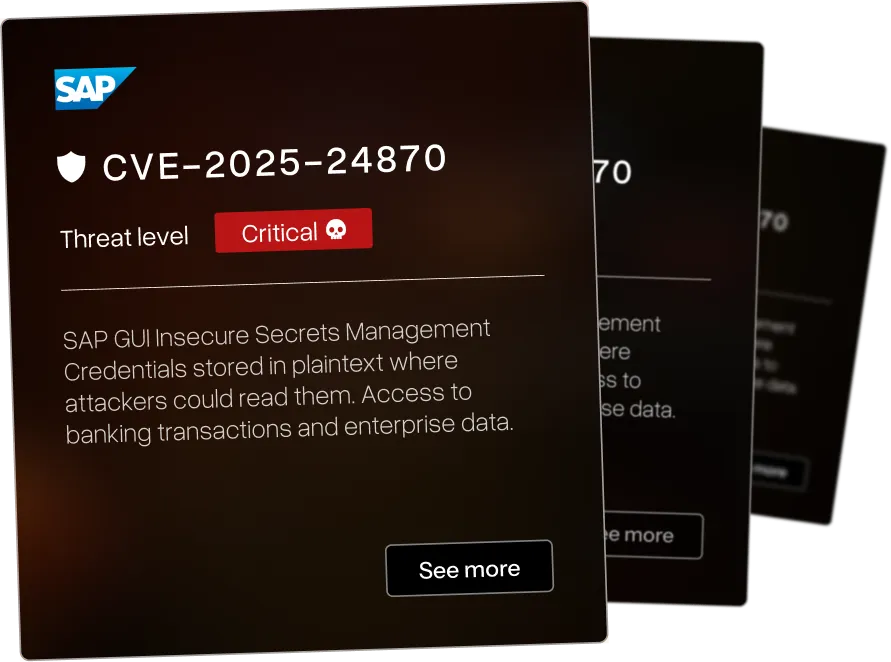
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


Cross-site scripting in Check Point Mobile Access portal SNX bookmarks allows attackers to inject malicious scripts via bookmark parameters






Directory traversal in Check Point Mobile Access File Share allows authenticated attackers to access files outside intended directories






Information disclosure via GraphQL introspection in OpenShift exposes API schema and internal structure to attackers






Denial of service vulnerability in OpenShift container platform allows attackers to disrupt cluster operations






Session fixation in SoftCOM iKSORIS Internet Starter Module allows attackers to hijack user sessions






Stored cross-site scripting in SoftCOM iKSORIS Internet Starter Module allows persistent malicious script storage






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module via additional vulnerable parameter






Open redirect in SoftCOM iKSORIS Internet Starter Module allows attackers to redirect users to malicious websites






Client-side denial of service in SoftCOM iKSORIS Internet Starter Module causes browser to become unresponsive




.webp)

Open redirect in MobSF login allows attackers to redirect authenticated users to malicious websites






PIN brute force vulnerability in KioWare for Windows due to missing rate limiting on PIN entry






Security control bypass in KioWare for Windows allows circumvention of kiosk restrictions






Kiosk environment escape in KioWare for Windows allows users to break out of restricted kiosk mode






Text injection vulnerability in Fortinet SSL VPN web UI allows attackers to inject arbitrary text content into the login page






IP spoofing vulnerability in Site Reviews WordPress plugin allows attackers to bypass IP-based restrictions




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.