What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
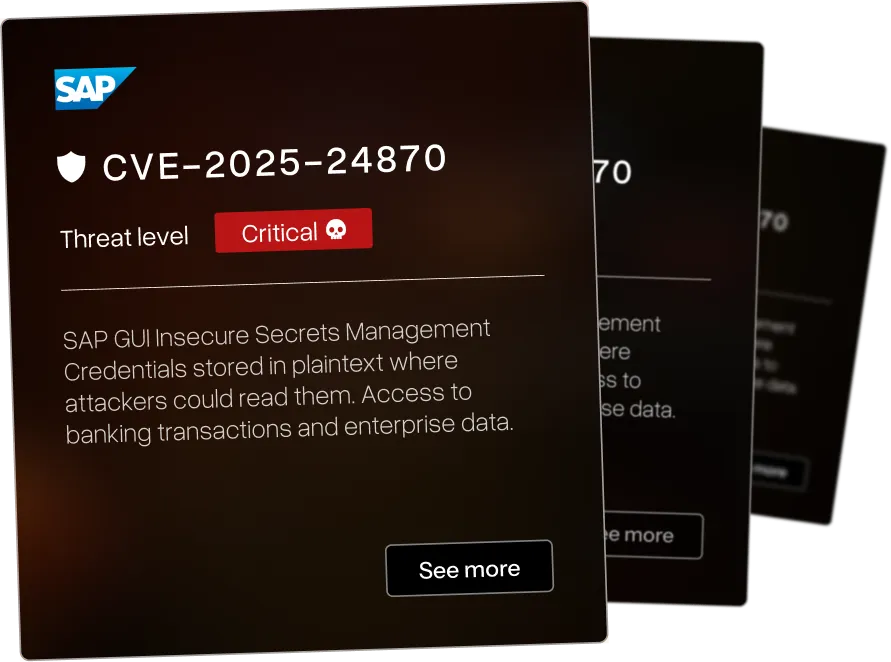
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.
.webp)

Stored cross-site scripting in IBM InfoSphere DataStage Designer allows persistent script injection affecting other users




.webp)

Stored cross-site scripting in IBM InfoSphere Information Server allows persistent malicious script storage




.webp)

Stored cross-site scripting in IBM InfoSphere Information Server via different injection point






DLL hijacking vulnerability in Check Point SmartConsole R82 allows local attackers to execute arbitrary code by placing malicious DLLs






Credential exposure via memory dump in Check Point SmartConsole allows local attackers to extract authentication credentials from process memory






Cross-site scripting in CKEditor4 preview feature allows script execution when previewing malicious content






Admin+ stored XSS in LuckyWP Table of Contents WordPress plugin allows administrators to inject persistent scripts




.svg.webp)

HTML injection in BMC Control-M enterprise job scheduler allows injection of arbitrary HTML content




.svg.webp)

DLL side-loading in BMC Control-M allows local attackers to execute arbitrary code via malicious DLLs




.svg.webp)

Incorrect authorization in BMC Control-M allows users to access functionality beyond their privilege level






Path traversal in Smartwares IP cameras allows remote attackers to read arbitrary files from the device filesystem






Shared default credentials across all Smartwares cameras - compromising one device provides access to all devices






Command injection in Smartwares IP cameras allows remote attackers to execute arbitrary system commands






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module via separate vulnerable endpoint






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module allows script execution via URL manipulation




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.