What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
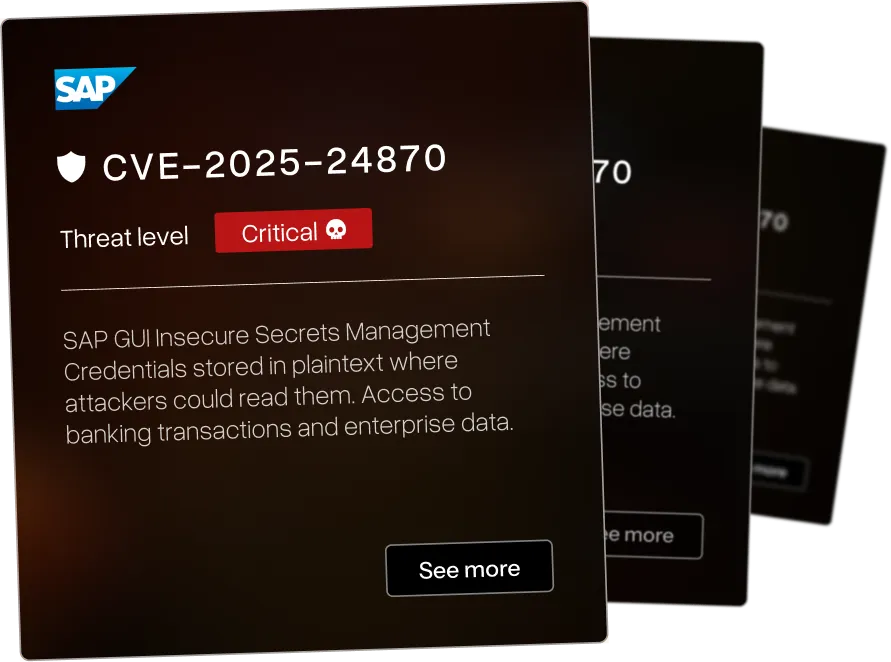
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.


Reflected cross-site scripting in Kentico CMS allows attackers to execute scripts via crafted URLs






Cross-site scripting in OpenText Advanced Authentication (NetIQ) allows attackers to inject malicious scripts into web pages






SQL injection in OpenText Advanced Authentication (NetIQ) allows unauthenticated attackers to execute arbitrary SQL commands against the database






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module via additional parameter






Stored cross-site scripting in SoftCOM iKSORIS Internet Starter Module allows persistent script injection






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module via different injection point






Reflected cross-site scripting in SoftCOM iKSORIS Internet Starter Module allows attackers to execute scripts via crafted URLs






Reflected cross-site scripting in Palo Alto Networks PAN-OS GlobalProtect portal allows script execution via crafted URLs






Unauthenticated cross-site scripting in POST SMTP Mailer WordPress plugin allows script injection without authentication






Admin+ stored XSS in Bookly WordPress plugin allows administrators to inject persistent malicious scripts






Stored cross-site scripting in Kofax Capture software allows persistent malicious script injection






Reflected cross-site scripting in SAS 9.4 allows attackers to execute scripts via crafted URLs





Admin+ stored XSS in Easy Forms for Mailchimp WordPress plugin allows administrators to inject persistent scripts




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code




.webp)

Decryption key disclosure in IBM i Access Client Solutions allows local attackers to obtain encryption keys via improper authority checks




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.