What This Vulnerability Research Portfolio Represents
Discoveries That Matter
Our vulnerability research team reverse engineers your enterprise software to find the 0-days that threaten your infrastructure - before attackers do.

Enterprise Focus
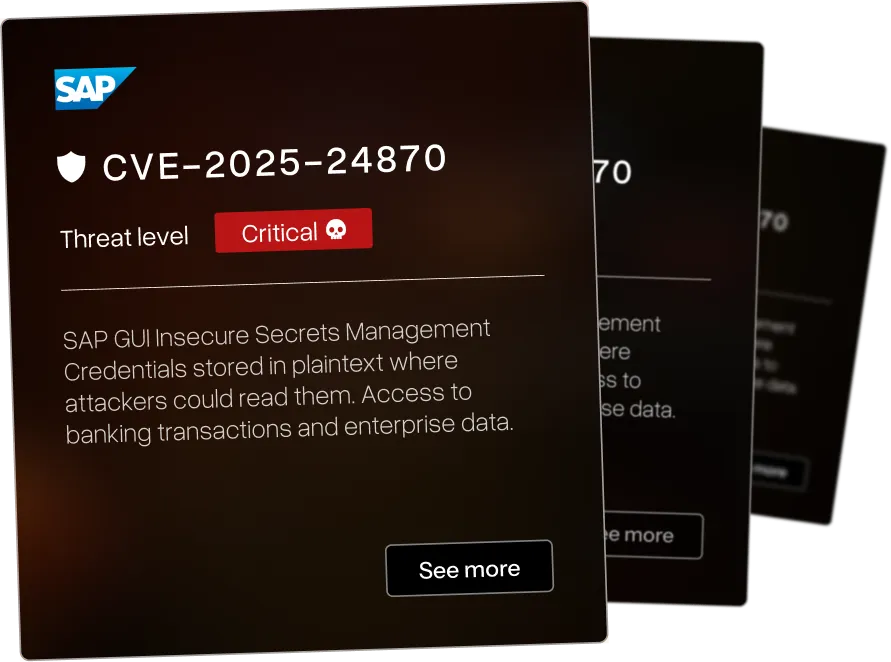
The vulnerabilities below affect systems organizations use: SAP. IBM. Check Point. F5. BMC. Microsoft. Rapid7. Cyberark.

Current Research
We identified a wide range of CVEs across various industries - each of the vulnerabilities have been assigned a threat level ranging from critical to low. We pride ourselves in beating others to identify critical CVEs in large infrastructure for orgasations such as IBM and Microsoft.
.webp)

Weak password encryption in IBM i Access Client Solutions allows attackers to decrypt stored passwords and access connected systems




.png)

Cross-site scripting in Spipu HTML2PDF example files allows script execution via crafted input






Denial of service in F5 BIG-IQ iControl SOAP daemon - attackers with guest privileges can crash the service






Reflected cross-site scripting in F5 BIG-IP Configuration utility allows script execution via crafted requests






Path traversal in elFinder PHP LocalVolumeDriver connector allows reading/writing files outside webroot






Windows Kernel elevation of privilege allows local attackers to escalate from user to SYSTEM level access (CVSS 7.8)




.webp)

Stored cross-site scripting in IBM Cognos Analytics via malicious SVG files in Custom Visualizations






Unauthenticated path traversal in Hummingbird WordPress plugin allows reading arbitrary files from the server






SQL injection in Sparx Systems Enterprise Architect allows attackers to execute arbitrary SQL queries




.webp)

DLL hijacking in IBM i Access Client Solutions on Windows allows local code execution via malicious DLLs






URL spoofing in OwnCloud password reset emails allows phishing attacks via manipulated reset links






Cross-site scripting in blog-post creation functionality in Amasty Blog Pro for Magento 2






Cross-site scripting in preview functionality in Amasty Blog Pro for Magento 2




.webp)

Stored cross-site scripting in IBM InfoSphere Information Server allows persistent malicious scripts






Stored cross-site scripting in blog-post creation in Amasty Blog Pro for Magento 2 allows persistent script injection




We map your systems before testing how they break.
That's why critical findings usually show up outside the original scope - attackers don't respect scope documents.
Security Assessment Services FAQ
Questions enterprise security teams ask before partnering with AFINE for security assessments.