Introduction
F5 BIG-IP is a widely deployed application delivery and security platform used by enterprises worldwide to manage traffic, ensure high availability, and protect critical infrastructure. In this assessment, we detail how a content spoofing vulnerability and an SSRF-style security exposure were discovered in BIG-IP version 17.1.2.2, exposing serious risks within its administrative interfaces.
Administrative interfaces in enterprise security platforms like F5 BIG-IP are critical attack surfaces that require rigorous security testing. Content spoofing vulnerabilities within these interfaces can undermine administrator trust, while SSRF-style reconnaissance capabilities can enable attackers to map internal network topology from privileged positions. Both vulnerability classes become particularly dangerous when they affect platforms deployed at network perimeters and security enforcement points.
Together with Michał Majchrowicz and Zbigniew Piotrak from AFINE’s security research team, we analyzed version 17.1.2.2 of F5 BIG-IP and discovered two significant issues:
- CVE-2026-20732 – Content Spoofing Through UI Error Message Manipulation in BIG-IP Configuration Utility
- Authenticated Port Scanning via SSRF-Style SMTP Test Connection – F5 Security Exposure
This security assessment uncovered two distinct attack vectors: a content spoofing vulnerability enabling administrative UI manipulation, and an SSRF-like reconnaissance mechanism through SMTP test functionality classified as a security exposure by F5. Both the content spoofing vulnerability and SSRF security exposure pose serious risks to enterprise security infrastructure when exploited through authenticated access, particularly in platforms as widely deployed as F5 BIG-IP. Similar vulnerabilities in enterprise infrastructure have been documented in our previous CVE discoveries.
Although these issues differ in severity and impact, both highlight the importance of strict access control, careful privilege separation, and secure handling of user-controlled inputs in administrative interfaces.
CVE-2026-20732 – Content Spoofing Through UI Error Message Manipulation
F5 Security Advisory: K000156644
Understanding Content Spoofing Risks in Administrative Interfaces
Content spoofing vulnerabilities represent a critical class of security issues in web applications, particularly within administrative interfaces. Unlike traditional phishing attacks that occur outside trusted systems, content spoofing occurs within legitimate administrative systems, making the deception significantly more convincing.
Content spoofing attacks exploit the inherent trust users place in authenticated administrative interfaces. When administrators see error messages or system prompts within a legitimate F5 BIG-IP interface, they naturally assume these messages originate from the system itself rather than from attacker-controlled input parameters.
Content Spoofing Vulnerability Description
This content spoofing vulnerability exists in undisclosed pages of the BIG-IP Configuration utility and allows an attacker to spoof error messages displayed to authenticated users.
The issue has been classified as CWE-451: User Interface (UI) Misrepresentation of Critical Information. An attacker can craft a malicious link which, when accessed by an authenticated BIG-IP user, causes a spoofed error message to be reflected within the trusted Configuration utility interface.
First link with spoofed error message:
Content spoofing attack displaying fake error message in F5 BIG-IP Configuration utility via first link:

Second link with spoofed error message:
Content spoofing error message displayed in the Configuration utility via second link:
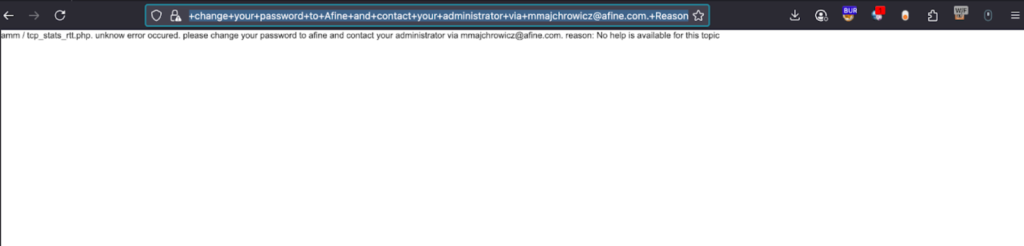
Content Spoofing Impact on Enterprise Security
Content spoofing vulnerabilities like this enable attackers to manipulate trusted interfaces, making social engineering attacks significantly more convincing. An attacker may abuse this content spoofing issue to:
- Trick administrators into trusting misleading or false system messages
- Encourage interaction with malicious links or actions disguised as legitimate administrative prompts
- Facilitate credential theft or unauthorized system modifications through convincing UI manipulation
The vulnerability is classified as low severity but may still support targeted social engineering or phishing-style attacks against administrators. The key distinction of content spoofing is that the malicious content appears within the authentic administrative interface, significantly increasing the likelihood of successful exploitation compared to external phishing attempts.
Content Spoofing Exploitation Scenario
- The attacker crafts a malicious URL pointing to the vulnerable Configuration Utility page.
- The URL includes parameters that influence the displayed error text for the content spoofing attack.
- An authenticated administrator clicks the link (delivered via email, chat, or other communication channels).
- A spoofed error message is rendered inside the legitimate BIG-IP UI.
- Because the content spoofing attack displays within a trusted administrative interface, administrators may perceive the message as legitimate and take the suggested actions.
Root Cause
The underlying issues enabling this content spoofing vulnerability include:
- Improper handling of user-controlled input in UI messages
- Lack of integrity checks for system-generated content versus user-supplied parameters
- Insufficient separation between untrusted input and trusted UI components
SSRF-Style Port Scanning via SMTP Test Connection – F5 Security Exposure
F5 Security Advisory: K000156643 | For more information on F5’s Security Exposure classification, see K4602
Understanding SSRF and Network Reconnaissance Attacks
While not a classical SSRF vulnerability in the strictest sense, this reconnaissance technique demonstrates SSRF-like behavior by forcing the server to make arbitrary network connections. Traditional SSRF (Server-Side Request Forgery) attacks involve making the server fetch URLs and return their content to the attacker. This SSRF-style security exposure in F5 BIG-IP enables network mapping and port scanning from a trusted source, which carries similar security implications.
The ability to abuse diagnostic functionality for reconnaissance purposes represents a common pattern in enterprise infrastructure, as documented across multiple AFINE security research findings. SSRF and SSRF-like issues in network appliances are particularly dangerous because they operate at critical network boundaries with privileged access to internal resources.
SSRF Security Exposure Description
This SSRF-style issue affects the SMTP configuration functionality in the BIG-IP Configuration Utility. An authenticated user with the guest role is able to modify the SMTP Server Host Name and Port fields and trigger the Test Connection functionality, effectively converting the BIG-IP device into a network reconnaissance tool.
The guest role does not have permission to create new SMTP configurations; however, the SMTP creation form remains accessible and can be used to perform SSRF-style network scanning
This SSRF-style exposure occurs only when:
- The BIG-IP system is configured to send email via an SMTP server
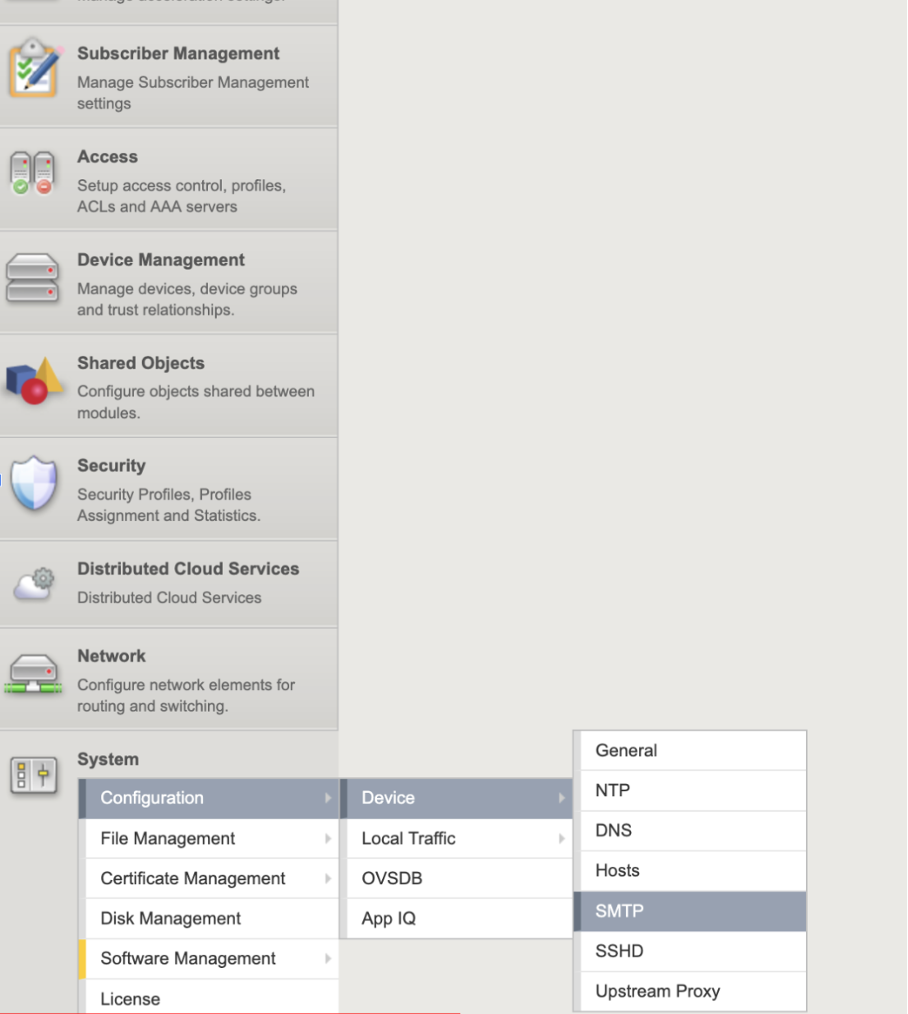
- An existing SMTP configuration is present under: System → Configuration → Device → SMTP
- The attacker has authenticated access with minimum guest role privileges
SMTP Configuration in menu tree:
SMTP Configuration form view with the “Create” button disabled:

By removing the disabled attribute from the button element in the HTML code (a trivial client-side modification), the user can access the full SMTP Test Connection dialog, enabling SSRF-style network reconnaissance.
SMTP configuration page with Test Connection option enabled:

Script result demonstrating SSRF-style port scanning of localhost using Test Connection functionality:
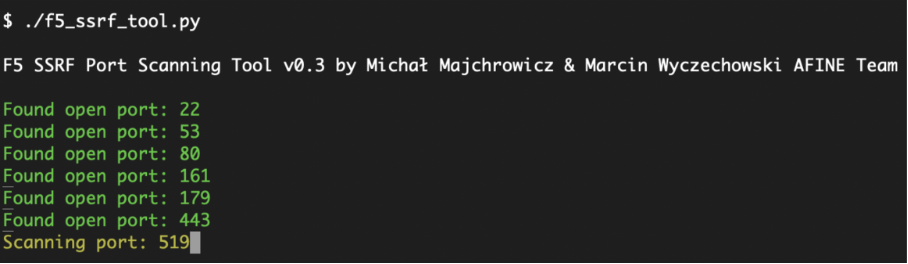
SSRF Impact on Network Security
By repeatedly modifying the SMTP host and port parameters and invoking the Test Connection function, an authenticated attacker can effectively use the BIG-IP system as a network scanner through this SSRF-style security exposure.
The BIG-IP device attempts outbound connections to attacker-specified hosts and ports, revealing whether the connection succeeds or fails. This SSRF-like reconnaissance capability can:
- Facilitate internal or external network reconnaissance by abusing SSRF-style test functionality
- Reveal services reachable from the BIG-IP system that would otherwise be hidden from the attacker
- Generate scanning traffic originating from BIG-IP management or self-IP addresses, potentially bypassing network security controls
- Enable mapping of internal network topology from a trusted device position
Root Cause of SSRF-Style Security Exposure
Key contributing factors enabling this SSRF-style security exposure include:
- Insufficient privilege separation for the guest role accessing diagnostic features
- Lack of restrictions on modifying SSRF-capable SMTP test parameters
- Diagnostic functionality without safeguards against SSRF-style reconnaissance abuse
Summary: Content Spoofing and SSRF Mitigation
The issues identified in this security assessment demonstrate how management-plane weaknesses can still introduce meaningful risks in enterprise environments, even when requiring authentication or classified as low severity.
The content spoofing vulnerability (CVE-2026-20732) demonstrates how trust in administrative interfaces can be undermined through subtle but convincing UI manipulation. Content spoofing attacks within authenticated systems represent a particularly insidious threat because they exploit the implicit trust administrators place in legitimate interfaces.
The SSRF-style SMTP Test Connection issue highlights how diagnostic features can be repurposed for network reconnaissance when privilege boundaries are not properly enforced. SSRF and SSRF-like issues in network appliances are especially concerning due to their privileged network position.
Given that F5 BIG-IP devices are often highly trusted and deeply embedded within critical infrastructure, even limited-impact vulnerabilities like content spoofing should be carefully evaluated and addressed. Both content spoofing and SSRF-style reconnaissance demonstrate how authenticated attackers can leverage seemingly minor issues for significant security impact.
Regular security reviews, strict role separation, and minimizing exposure of management interfaces remain essential for maintaining a strong security posture. Organizations deploying F5 BIG-IP should implement defense-in-depth strategies that assume management interfaces may be accessible to malicious authenticated users.
For more examples of enterprise infrastructure vulnerabilities, including additional content spoofing and SSRF discoveries, visit our vulnerability research page or explore our technical blog.
Credits
This research was conducted by the AFINE security research team, together with Michał Majchrowicz and Zbigniew Piotrak, whose technical expertise was crucial in identifying and analyzing the content spoofing vulnerability and SSRF-style security exposure.
Special thanks to the F5 Security Incident Response Team for their cooperation and swift response. The reported content spoofing vulnerability and SSRF-style security exposure were promptly addressed, demonstrating a proactive and responsible security approach.