HIPAA Penetration Testing
for Healthcare
Healthcare Penetration Testing by Researchers With 150+ Published CVEs and 10 Years of Experience Testing Medical Institutions
HIPAA Penetration Testing That Reduces Risk
Why most healthcare penetration testing fails to reduce risk:
Development teams get reports they can't act on
Security leaders spend weeks arguing about priorities
Boards receive technical documents without business context
We show you what breaks, how it breaks, and what customer data is exposed
Why Healthcare Enterprises Choose AFINE for HIPAA Penetration Testing
We've spent 10 years penetration testing major European healthcare institutions in production and found hundreds of critical vulnerabilities. You get researchers who know what breaks in EHR systems and medical infrastructure, and reports that show exactly how we exploited your environment. Each finding includes working proof-of-concept and business impact.

Our Services
What We Cover in Healthcare Penetration Testing
Patient Portals and Telehealth Platforms
We assess security of patient portals and telehealth platforms - targeting video sessions, API endpoints, and EHR integrations. Testing focuses on data protection mechanisms and unauthorized access to medical documentation.

Mobile Health Applications
We assess mobile health app security - authentication, authorization, and how PHI data is stored. Testing includes encryption implementation quality, traffic interception possibilities, and security on compromised devices.

Healthcare APIs and HL7 Interfaces
We enumerate endpoints and test authorization boundaries between users and patient records. Analyze data flows under concurrent load for race conditions. Check business logic flaws specific to medical data processing. Test API authentication and rate limiting.

EHR/EMR and Core Systems
We simulate breach scenarios from internet-facing systems to core infrastructure. Test network segmentation, privilege escalation paths, and database access controls. Review source code for custom healthcare applications - memory corruption, type conversion issues, and race conditions.

Third-Party Integrations and Medical Devices
We assess security at integration points and trust boundaries. Test authorization across partner connections and health information exchange security. Evaluate medical IoT infrastructure including infusion pumps, patient monitors, and imaging systems. Check whether IT and medical device networks are actually segregated.

Medical Device and Hardware Security Testing
We test physical devices and embedded systems. Analyze medical device firmware, diagnostic equipment, HSM configurations, and wireless protocols. Test for backdoors, unauthorized code, communication protocol vulnerabilities, and resistance to physical attacks. Hardware compromises persist longer than software bugs.

Social Engineering Testing for Healthcare
We run spear phishing against privileged users, phone-based social engineering, and physical access attempts. Insider threat simulations show what happens when legitimate access gets abused. Test employee awareness with realistic scenarios specific to healthcare operations and actual user access levels.

The Enterprise Security Software We Hacked
Our healthcare penetration testing researchers discover vulnerabilities in medical platforms running critical operations. We exploit both known CVEs and the vulnerabilities nobody's documented yet.


Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code






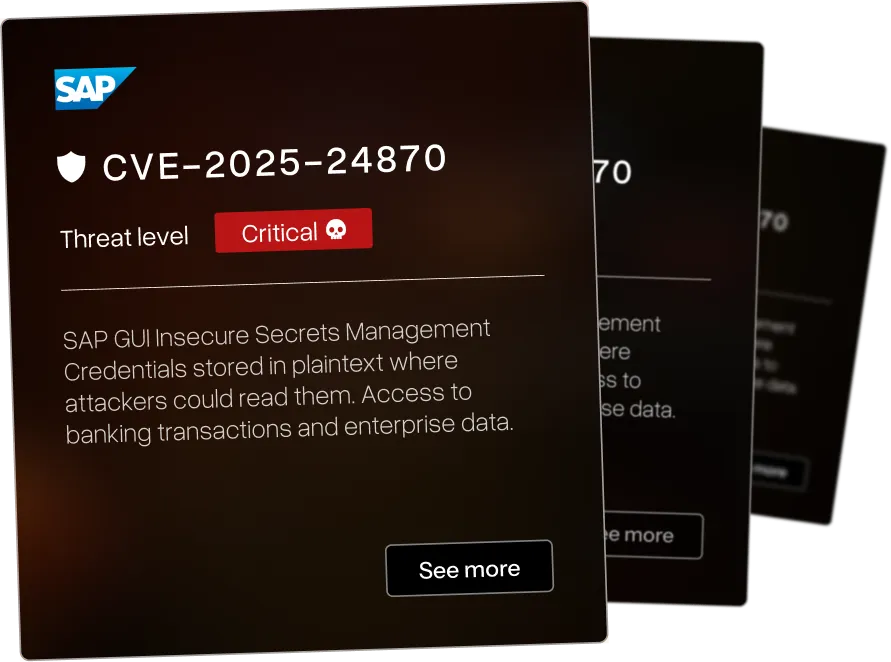
Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts




View All CVEs We've Published
.webp)


.webp)
The AFINE Adaptive Security Framework (AASF)
A framework developed from a decade of security assessments and continuously refined as attack methods evolve. Our methodology reflects current threat patterns and the practical security decisions organizations face as their attack surface expands.
We’re ready to deliver next-level security
Why Organizations Trust Us
Healthcare Penetration Testing FAQ
Let's Discuss Your Security Posture
We scope every HIPAA compliance testing engagement based on your systems and regulatory requirements. Book an assessment below to discuss your needs.