Introduction
VoIP has become the backbone of modern enterprise communication, delivering unmatched flexibility and cost efficiency. However, its dependence on internet-based networks also presents distinct cybersecurity challenges. This article explores VoIP’s basics, infrastructure, components, and protocols, examines common threats, and highlights the role of VoIP penetration tests in safeguarding organizations against evolving threats.
What is VoIP?
VoIP stands for Voice over Internet Protocol, also known as IP telephony or Internet telephony. It is a set of technologies that transmit voice, video, and multimedia content over the Internet Protocol instead of traditional circuit-switched telephone systems. VoIP enables real-time communication across devices, including IP phones, computers, and mobile apps, by converting analog voice signals into digital data packets.
Its adoption is driven by cost savings, unified communications (UC) systems integration, and support for advanced features like video conferencing. VoIP enables seamless integration with business applications like CRM platforms and collaboration tools. However, this advancement introduces unique security challenges, making VoIP penetration testing essential to ensure system integrity and protect sensitive communications.
Key Functionalities of VoIP Systems
- Call forwarding, queuing, and recording
- Welcome messages and IVR
- Audio and video conferencing
- Voicemail service
- Integration with business tools like CRM
- Support for remote work by using desktop and mobile apps (location independence)
- Scalability and flexibility
- Cost reduction
VoIP Infrastructure
A VoIP system primarily consists of a Private Branch Exchange (PBX), a central server managing voice communication between users and endpoints—devices or applications facilitating connectivity with the PBX. However, VoIP architecture has multiple implementations based on infrastructure, protocols, and deployment models. Below are the key components of the VoIP infrastructure.
PBX (Private Branch Exchange)
PBX is the main element for any VoIP implementation. It is a private telephony system that manages internal and external voice communications. It handles call routing, switching, and other advanced telephony features. There are various implementations that PBX can take, including:
- On-premises PBX – a physical VoIP server hosted locally on the organization’s infrastructure.
- Virtualized PBX – a lightweight, software-based PBX running on a virtual machine.
- Cloud-based PBX – a hosted VoIP service managed off-site by a third-party service provider, eliminating the need for on-site infrastructure.
Endpoint Devices
Among the endpoint devices, we can mention:
- IP Phones – hardware devices, physical desk phones designed for VoIP communication.
- Softphones – software-based applications that run on desktops, tablets, or smartphones, enabling voice communication over IP networks.
- Analog Telephone Adapters (ATAs) – devices for connecting traditional analog telephones, fax machines, and similar customer-premises devices to a VoIP network.
Gateways
Gateways are critical components in VoIP infrastructures that enable interoperability between disparate telecommunication networks. They bridge the gap between different types of networks e.g. Public Switched Telephone Network (PSTN) with IP-based networks, ensuring seamless voice, video, and signaling communication. Gateways are categorized into media gateways and signaling gateways, each serving distinct yet complementary roles.
- Media Gateways – handle voice/video traffic conversion between different network formats and protocols.
- Signaling Gateways – focus on protocol translation for call control and session management.
Session Border Controllers (SBC)
Session Border Controllers (SBCs) are critical components of VoIP networks. They ensure the security, regulation, and optimization of communication flows. Their key functions include:
- Security and firewall protection
- Quality of Service (QoS) management
- Multi-vendor interoperability
- Call handling and policy enforcement
- Protocol interworking
- Monitoring and reporting
VoIP Protocols
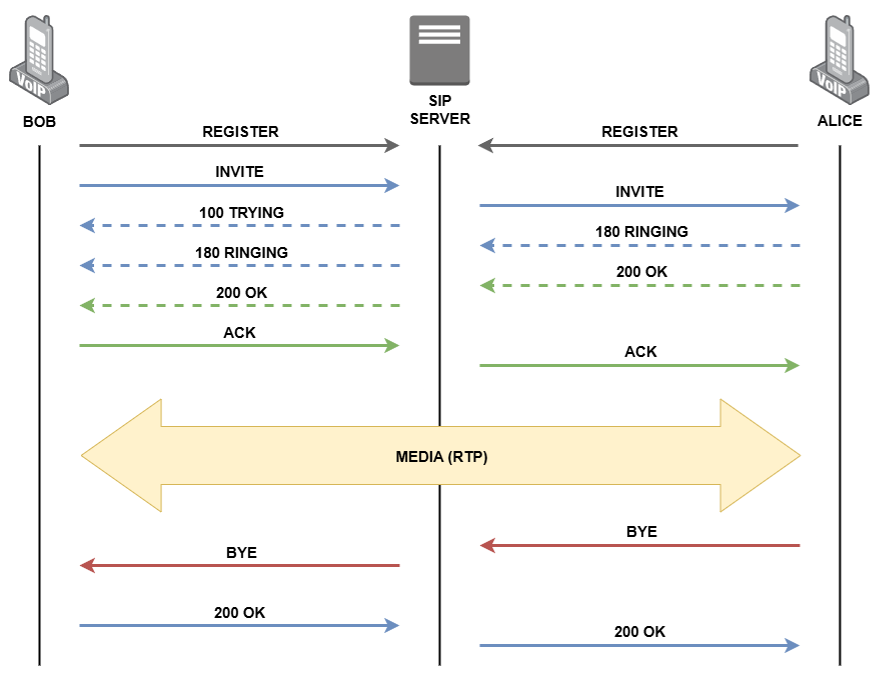
SIP (Session Initiation Protocol)
SIP is a signaling protocol that initiates, maintains, modifies, and terminates real-time communication sessions over IP networks. These sessions can involve voice calls, video calls, messaging, and other multimedia communications. SIP is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol (HTTP). By default, SIP uses port 5060 UDP/TCP for unencrypted traffic or port 5061 UDP/TCP for TLS-encrypted traffic.
Requests
There are fourteen SIP request methods of which the first six are the core requests.
Core SIP methods:
- REGISTER – tells a SIP server that a user is ready to receive calls their location (e.g., current IP address).
- INVITE – starts a new communication session (voice or video call).
- ACK – confirms that an INVITE request was successfully received.
- CANCEL – cancels an unanswered INVITE before the call is connected.
- BYE – ends and active call/session.
- OPTIONS – query endpoint what capabilities it supports.
Additional SIP methods:
- PRACK – confirms receipt of temporary responses (1xx), increasing the reliability of signaling.
- SUBSCRIBE – initiates a subscription for notification of events from a notifier.
- NOTIFY – informs a subscriber of notifications of a new event.
- PUBLISH – publishes an event to a notification server.
- INFO – sends mid-session information that does not modify the session state (e.g., DTMF).
- REFER – asks the recipient to establish a connection with a third party, often used for call forwarding.
- MESSAGE – sends an instant message over SIP, similar to an SMS.
- UPDATE – modifies session parameters.
Responses
SIP Requests are answered with SIP responses, of which six classes exist.
- 1xx – informational responses, such as 180 (ringing).
- 2xx – success responses.
- 3xx – redirection responses.
- 4xx – request cannot be completed at the server (e.g., bad request syntax, code 400).
- 5xx – valid request cannot be completed by the server (e.g., internal server error, code 500)
- 6xx – request cannot be completed at any server – global failure.
Simple Interaction Structure
Bob is calling Alice.
RTP (Real-time Transport Protocol)
The Real-time Transport Protocol (RTP) is a standardized network protocol designed for the real-time transmission of audio and video over IP networks. Developed by the Audio/Video Transport Working Group of the Internet Engineering Task Force (IETF), RTP was first defined in IETF RFC 1889 and later updated in RFC 3550. As the primary protocol for streaming media, RTP plays a crucial role in communication and entertainment systems, including VoIP.
RTP is primarily used over UDP to minimize latency and typically operates on high-numbered dynamic ports assigned for media transmission in SIP-based communications. This flexibility and efficiency make RTP the leading protocol for real-time media transport in modern IP-based networks.
The Role of VoIP Penetration Tests in Organizational Security
A penetration tester’s objective is to methodically replicate adversarial actions to identify exploitable vulnerabilities before malicious actors do. This involves simulating real-world attack scenarios – from reconnaissance to exploitation – to validate whether security controls effectively mitigate risks. In VoIP environments, pentesters focus on protocols (e.g., SIP, RTP), endpoints (e.g., IP phones, softphones), and supporting infrastructure (e.g., PBX, gateways) to uncover weaknesses such as misconfigurations, weak authentication, or insufficient encryption.
Conducting actions like enumeration, network segmentation tests, or configuration review, pentesters provide actionable insights into an organization’s defensive posture. Crucially, penetration testing goes beyond vulnerability scanning; it contextualizes risks by demonstrating how chained exploits could lead to unauthorized call routing, financial fraud, or data exfiltration.
Common VoIP Threats
This section delves into prevalent VoIP-specific threats, dissecting their technical underpinnings and exploitation pathways. To effectively assess security risks, penetration testers must thoroughly examine each aspect of the VoIP infrastructure, simulating real-world attack scenarios and replicating malicious actions. This approach ensures a comprehensive evaluation of vulnerabilities and helps organizations strengthen their defenses against evolving threats.
Enumeration and Information Gathering
Attackers begin by collecting as much information as possible about the target VoIP system. This includes identifying SIP (Session Initiation Protocol) servers, IP addresses, extensions, and device configurations. By analyzing network traffic and using various tools, scanners, and scripts, an attacker can map out the topology and gain insight into system components, which in turn can inform more targeted exploits. This reconnaissance phase is crucial since even seemingly benign information can later be used to uncover vulnerabilities in configuration or implementation.
Authentication Attacks
VoIP systems require authentication to initiate and manage calls. However, if the authentication mechanisms are not robust, attackers can employ brute-force techniques to guess passwords. Automated scripts can attempt thousands of password combinations in a short time, especially if the system lacks account lockout policies or rate limiting.
It is often the case that call initiation does not require authentication, a vulnerability that attackers can exploit to impersonate an organization and place fraudulent calls on its behalf. This lack of verification enables malicious actors to spoof caller identities, potentially damaging the organization’s reputation, deceiving recipients, or facilitating social engineering attacks.
Outdated and Vulnerable Software
Many VoIP solutions run on software platforms that, if not regularly updated, can harbor known vulnerabilities. Outdated systems might miss critical security patches, leaving them open to exploits that target flaws in protocol implementations or configuration weaknesses.
Attackers exploit these vulnerabilities to gain unauthorized access or to inject malicious code into the communication channels. Regular maintenance and patch management are essential to mitigate these risks.
Denial of Service (DoS)
VoIP systems are especially susceptible to Denial of Service attacks, where an attacker floods the network with excessive signaling or media traffic, effectively overwhelming the system. DoS attacks can target SIP servers, causing legitimate call setup requests to be delayed or dropped. In extreme cases, the service may become entirely unavailable, severely disrupting business communications.
Attackers might leverage amplification techniques or botnets to maximize the impact of their attack, underscoring the need for robust network defense strategies.
Unauthorised Calling (Toll Fraud)
Unauthorised calling, often known as toll fraud, involves an attacker gaining access to a VoIP system to make outbound calls without permission. Once inside the system, the attacker can exploit vulnerabilities or misconfigurations to route calls, potentially accruing significant charges or facilitating further fraudulent activities. Effective call authorization mechanisms and monitoring of call patterns are essential to detect and prevent such misuse.
Eavesdropping and Information Disclosure
VoIP communications, if not properly secured, can be intercepted by malicious actors. Eavesdropping involves the unauthorized capturing of both signaling and media streams. Attackers can exploit weaknesses in encryption protocols or leverage unsecured Wi-Fi networks to capture call content, which may include sensitive personal or business information. Ensuring end-to-end encryption and robust key management practices are critical to safeguarding VoIP communications from interception.
Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack occurs when an attacker positions themselves between two communicating VoIP endpoints – such as a SIP client and a SIP server – without either party knowing. This allows the attacker to intercept, modify, or inject malicious packets into the communication stream. In the context of VoIP, a MitM attack can have severe consequences, including call hijacking, credential theft, and service disruption.
Default and Weak Passwords
Using default or weak passwords remains a common vulnerability in many VoIP deployments. Default credentials, if not changed, provide an easy entry point for attackers. Even when non-default passwords are used, weak passwords can be quickly compromised through brute-force or dictionary attacks. It is imperative to enforce correct password policies and, where possible, implement multi-factor authentication to significantly reduce this risk.
Incorrect Network Segmentation (VLAN Hopping)
Proper network segmentation is a critical security practice, particularly in environments where voice and data networks coexist. Incorrectly configured VLANs or poor segmentation practices can allow an attacker to move laterally within the network (VLAN hopping), gaining access to sensitive VoIP signaling and media traffic. Effective segmentation and the implementation of strict access controls help contain breaches and limit the impact of an attack.
Final Words
VoIP security is a critical yet often overlooked aspect of an organization’s overall cybersecurity posture. Conducting VoIP penetration testing is a fundamental component of safeguarding VoIP environments. By systematically identifying vulnerabilities, organizations can proactively mitigate risks and reinforce the confidentiality, integrity, and availability of their communication systems.
The dynamic nature of technology necessitates continuous security assessments to address emerging threats and ensure that VoIP systems remain resilient against evolving attack techniques. Without regular evaluations, organizations risk exposing their communications infrastructure to potentially devastating security breaches.