As financial institutions grapple with the increasing complexity of cyber threats, Threat-Led Penetration Testing (TLPT) under the Digital Operational Resilience Act (DORA) has become an essential process for ensuring robust digital resilience. TLPT is not just a compliance requirement; it is a high-impact tool for simulating real-world cyberattack scenarios that test an organization’s capacity to detect, protect, and respond to sophisticated threat actors.
Our TLPT offering provides comprehensive support across key phases of Threat-Led Penetration Testing, including Threat Intelligence, Testing Phase, and Results Presentation. We conduct detailed threat analysis to create realistic attack scenarios, followed by scenario-based red teaming to evaluate the resilience of your organization’s critical systems. Upon completion, we deliver an in-depth report with actionable insights and recommendations, helping to strengthen your defenses against advanced cyber threats.
If you want to get familiar with TLPT under DORA, continue reading. If you want to see what we can do for your organisation, scroll directly to our offer or contact us.
Key Components of TLPT Process
Threat-Led Penetration Testing (TLPT) is a critical component of the Digital Operational Resilience Act (DORA) designed to reinforce cybersecurity resilience within financial institutions across the EU. TLPT involves simulating realistic cyberattack scenarios to assess an organization’s capacity to detect, protect, and respond to sophisticated threats. By incorporating real-world threat intelligence, TLPT provides a thorough assessment of an organization’s readiness to face targeted attacks. The TLPT process is structured into three key phases:
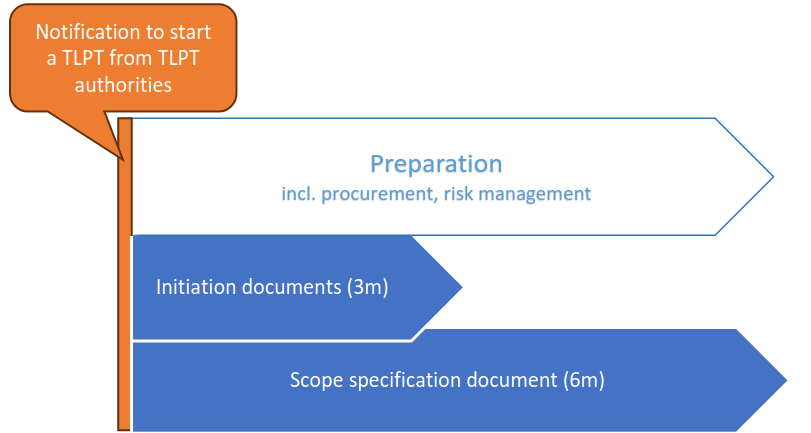
I. Preparation Phase
The first step in TLPT involves scoping the test to define critical systems, processes, and personnel. This phase sets the parameters for the test, including engagement with a Threat Intelligence (TI) provider to gather insights into specific threats relevant to the organization. It also involves establishing the white team (a small group aware of the test to avoid unintentional disclosures) and appointing certified TI and red-team providers to conduct the exercise. At this stage, clear communication channels are established, and a secure environment is created for handling sensitive information.
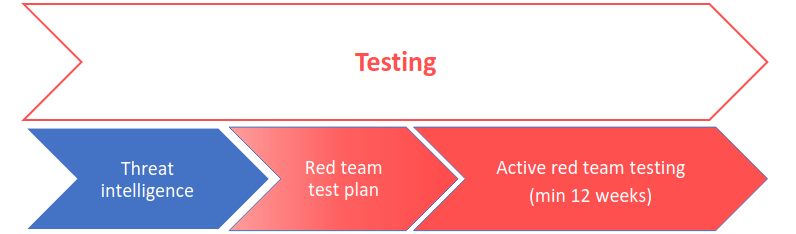
II. Testing Phase
The core of the TLPT process, the Testing Phase, involves a red-team simulation based on the gathered threat intelligence. This phase consists of covert, intelligence-driven cyberattacks that mirror the tactics, techniques, and procedures (TTPs) of real threat actors targeting critical functions within the organization. Conducted without the prior knowledge of the blue team (defenders), this phase assesses the effectiveness of an organization’s detection, response, and recovery mechanisms in a controlled, realistic scenario.
During the Testing Phase, the red team aims to breach systems, access sensitive data, and test the resilience of critical functions across people, processes, and technology. The exercise evaluates not only technical defenses but also the organization’s broader security posture, including its incident response capabilities.
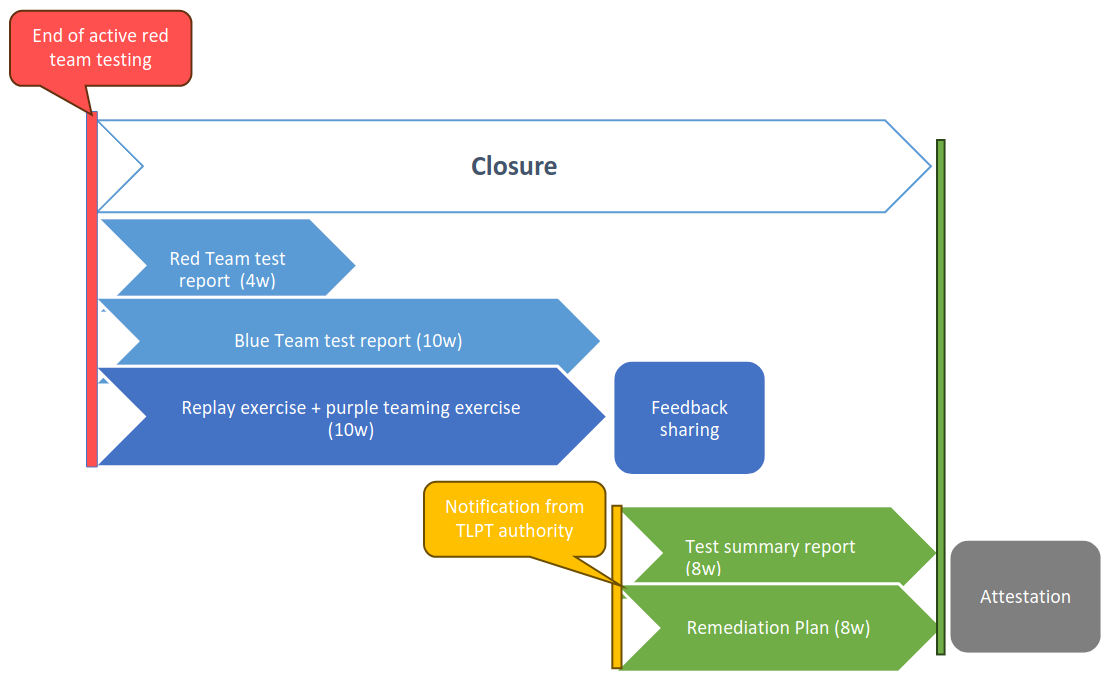
III. Closure and Remediation Phase
Following the testing, the Closure Phase involves comprehensive reporting and analysis. The red team presents its findings to the white team and relevant stakeholders, detailing identified vulnerabilities, and response effectiveness. The final report includes a thorough analysis of resilience gaps and recommendations for remediation, helping the organization strengthen its cybersecurity defenses. This phase often concludes with a collaborative session to plan for remediation and discuss strategies for enhancing resilience against future threats.
TIBER-EU Framework Integration
TIBER-EU framework provides a standardized methodology for TLPT across the EU financial sector. TIBER-EU’s structured phases (Preparation, Testing, and Closure) ensure that TLPT exercises align with both DORA’s standards and cross-border regulatory requirements. This is especially advantageous for multinational financial institutions, as TIBER-EU’s recognition protocols allow for streamlined testing that is compliant across jurisdictions.
AFINE services in TLPT’s Testing Phase
We provide comprehensive services covering all three phases of the TLPT process, in full compliance with DORA requirements. Our offer includes professional Threat Intelligence, Red Teaming, and Detailed Reporting, ensuring a thorough evaluation of your organization’s cybersecurity resilience. With our services, financial institutions can complete the full TLPT process, encompassing the Preparation Phase, Testing Phase, and Closure and Remediation Phase.
Threat Intelligence – Preparation Phase
In the Preparation Phase, our team gathers and analyzes in-depth Threat Intelligence, forming the foundation for creating realistic test scenarios. Our Threat Intelligence services focus on:
- Customized Threat Analysis: We identify potential threat actors and analyze their tactics, techniques, and procedures (TTPs), enabling us to develop attack scenarios tailored to the specific profile of the institution.
- Contextual Threat Landscape: Our intelligence work reflects the unique risk landscape of the financial sector, taking into account regulatory, operational, and technological requirements affecting the institution’s risk profile.
- Scenario Development: Leveraging gathered intelligence, we craft detailed attack scenarios that closely reflect current threats, enhancing the accuracy and relevance of the upcoming testing phase.
Red Teaming – Testing Phase
In the Testing Phase, our team conducts advanced red teaming simulations, applying Threat Intelligence insights in realistic scenarios. Our red teaming approach includes:
- Realistic Attack Execution: Our red team performs covert, scenario-based attacks targeting the organization’s critical assets, processes, and personnel, allowing for an authentic assessment of detection and response capabilities.
- Comprehensive Vulnerability Assessment: We evaluate technological, organizational, and response vulnerabilities across critical functions, providing a holistic view of the organization’s cybersecurity posture.
- Incident Response Analysis: We observe and assess the blue team’s (defense team’s) responses to simulated attacks, identifying key areas for strengthening and optimizing defensive measures.
Reporting and Remediation – Closure Phase
After completing the red teaming tests, we deliver a detailed report covering the simulation results, including identified vulnerabilities, and an assessment of the organization’s response capabilities. Our report includes:
- In-Depth Analysis of Findings: We provide comprehensive insights into security gaps and the effectiveness of current protective processes.
- Remediation Recommendations: Our recommendations offer clear guidance to help the organization reinforce its defenses and better prepare for future threats.
- Consultative Sessions: We conduct sessions with key stakeholders to review findings and collaboratively develop a remediation strategy.
With our support throughout each stage of TLPT, AFINE’s services provide full-cycle resilience-building against advanced cyber threats. Our approach ensures not only DORA compliance but also a long-term reinforcement of the organization’s digital defenses.
Why Choose AFINE TLPT Service for DORA Compliance?
Our TLPT service is uniquely designed to deliver value beyond compliance, offering our overall cybersecurity experience, while meeting DORA and TIBER-EU requirements. Here’s what sets us apart:
- Expertise: Our team comprises certified cybersecurity professionals with extensive experience in red-team testing and threat intelligence.
- Industry Experience: AFINE has extensive experience working with financial institutions, whose unique requirements demand a comprehensive approach to digital security. We have conducted numerous audits that identified critical vulnerabilities in banking systems, thereby eliminating many threats that could become targets for cybercriminals.
- Assured Compliance: We deliver a DORA-compliant TLPT process that not only satisfies regulatory requirements but also sets a standard for industry best practices in cybersecurity.
- Tailored Scenarios and Actionable Insights: Our approach focuses on delivering realistic, actionable results, with tailored threat scenarios and remediation plans that align with your organization’s unique threat landscape and operational structure.
- Value over Compliance: Although working with an extensive framework, our overall goal is simple: ensure that the cybersecurity threats in your organization are minimized to the lowest possible level.
Get Started with TLPT Today
Our TLPT services will provide your financial institution with the tools, insights, and strategic direction necessary to meet DORA’s requirements and improve your cybersecurity resilience. Contact us to learn how our comprehensive TLPT offerings can help you safeguard your organization and achieve compliance with DORA and TIBER-EU standards.


 TLPT under DORA
TLPT under DORA