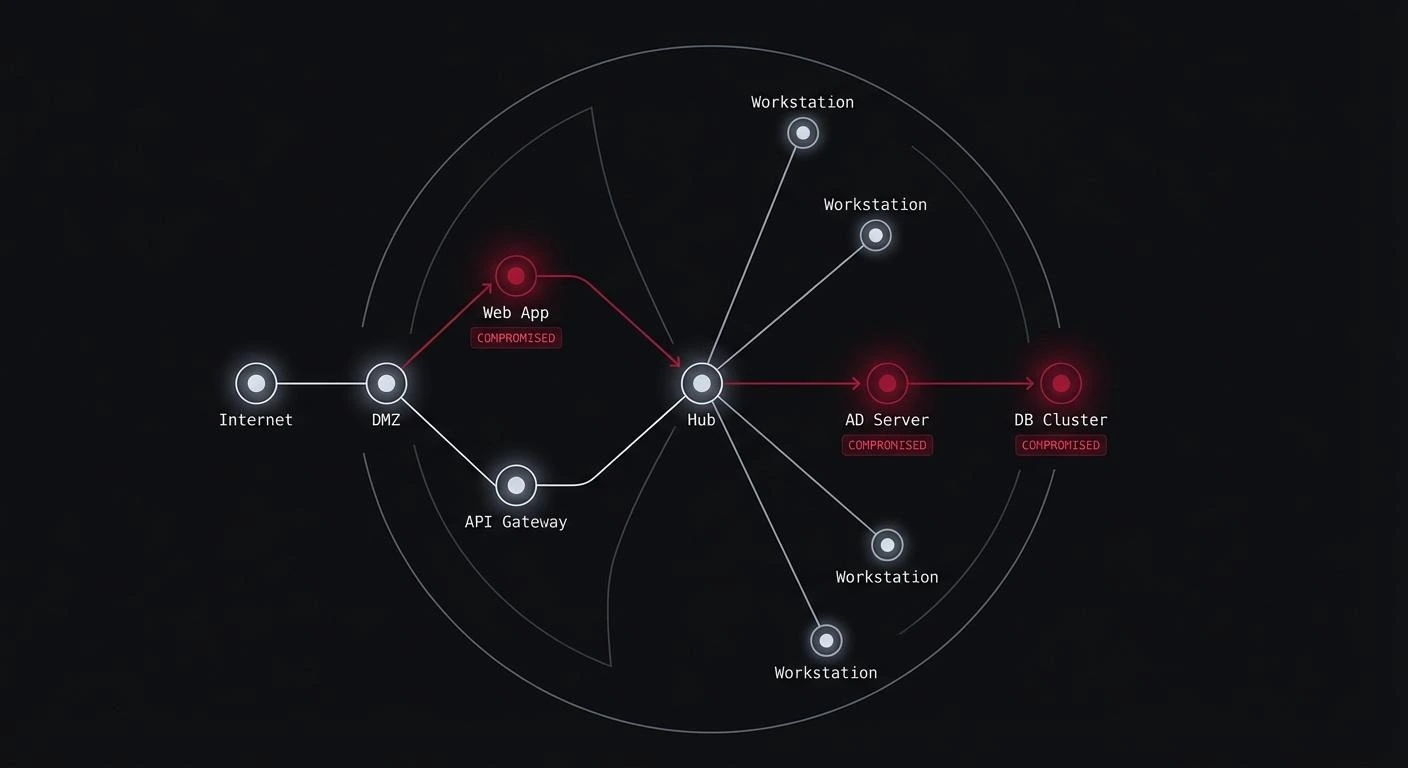
Thick-client penetration testing is a critical gap in most enterprise security programs. Banking software, trading platforms, healthcare systems, and manufacturing tools – these desktop applications handle your organization’s most sensitive data and critical operations.
But when was the last time you actually tested their security?
If you’re relying on the same penetration testing approach you use for web apps, you’re missing most of the attack surface. Thick clients don’t play by web application rules.
What Makes Thick Client Penetration Testing Different?
Thick client pentesting isn’t just “web app testing on a desktop.” The attack surface is fundamentally different.
Local execution means direct access. Attackers can attach debuggers to running processes, dump memory to analyze secrets, modify binaries before execution, and reverse engineer your entire codebase. No WAF will save you. No server-side validation catches these attacks.
File system access is unrestricted. Thick clients read and write across the entire file system. Configuration files sit in predictable locations. Cached data lives locally. Credentials might be stored in registry keys or preference files. Each storage point is a potential goldmine for attackers.
Multiple communication channels create complexity. You’re not just testing HTTP requests. Thick clients communicate via REST APIs, SOAP services, custom protocols, inter-process communication, and database connections. Each channel needs separate security validation.
The Three-Tier Architecture of Thick Client Apps
Understanding thick client architecture is essential for effective penetration testing.
Tier 1: The Presentation Layer
This is what users see and interact with. The UI layer seems innocent, but it’s where most security assumptions break down.
Many developers implement security checks at the UI level – disabling buttons, hiding menu items, and validating inputs in forms. These controls are trivial to bypass. An attacker can modify the binary, patch the executable at runtime, or call backend functions directly through debugging.
What to test: Input validation effectiveness, password field masking, clipboard operations, screenshot protection, error message information disclosure, and whether UI security controls are the only defense.
Tier 2: The Application Logic
Here lies your business logic – the core functionality that processes data, makes decisions, and enforces rules.
In two-tier architectures, this logic runs entirely on the client. In three-tier architectures, it is split between client and server. Either way, any logic running client-side is vulnerable to manipulation.
What to test: Authentication mechanisms, authorization enforcement, cryptographic implementations, license validation, business logic flaws, and whether critical security decisions happen client-side.
Tier 3: The Data Layer
Databases, file storage, and configuration management. Where sensitive data lives and how it’s protected.
Thick clients often store data locally – cached credentials, configuration files, temporary data, logs. They also connect to databases, sometimes with hardcoded connection strings or embedded credentials.
What to test: Local data encryption, database connection security, SQL injection vulnerabilities, credential storage mechanisms, and data leakage through logs or temp files.
Thick Client Penetration Testing Methodology
Here’s a systematic approach to thick client security assessment:
Phase 1: Information Gathering
Start by understanding what you’re dealing with.
Identify the application architecture. Two-tier or three-tier? What technologies are used? Which frameworks? What database backend? This determines your attack vectors.
Map the attack surface. Network connections, local file storage, registry keys, inter-process communication channels, and hardware interactions. Document everything the application touches.
Understand the authentication model. How does the app verify users? Local credentials? Domain authentication? Smart cards? Biometrics? Online/offline capabilities?
Tools you can use: Process Monitor, Wireshark, Fiddler, IDA Pro or Ghidra for static analysis.
Phase 2: Network Traffic Analysis
Thick clients aren’t isolated – they communicate. Start by intercepting that communication.
Configure your proxy correctly. Tools like Burp Suite or OWASP ZAP work for HTTP/HTTPS, but thick clients might use custom protocols. You may need Wireshark or Echo Mirage for non-HTTP traffic.
Look for certificate validation issues. Does the app accept self-signed certificates? Can you perform man-in-the-middle attacks? Many thick clients skip proper TLS validation.
Analyze the protocol. Is sensitive data transmitted in clear text? Are session tokens properly randomized? Can you replay requests? Are there hidden API endpoints?
Test API security. Authentication bypass, broken authorization, injection attacks, and excessive data exposure. Standard OWASP API testing applies here.
Common findings: Hardcoded API keys, weak encryption, cleartext credentials in transit, and replay attack vulnerabilities.
Phase 3: Client-Side Security Analysis
Now dig into the application itself.
Static analysis first. Decompile or disassemble the application. Look for hardcoded credentials, API keys, encryption keys, connection strings, and logic flaws.
Tools: .NET Reflector or dnSpy for .NET apps, JD-GUI for Java, Hopper or IDA Pro for native code.
Memory analysis. Attach a debugger (x64dbg, WinDbg, GDB) and dump memory while the application runs. Search for passwords, session tokens, encryption keys, and sensitive data.
File system forensics. Where does the app store data? Check AppData directories, ProgramData, registry keys, and temp folders. Look for:
- Configuration files with credentials
- Cached authentication tokens
- Unencrypted sensitive data
- Insecure file permissions
Dynamic analysis. Modify the application’s behavior at runtime. Bypass license checks, escalate privileges, and disable security controls. Tools like Frida for hooking, or manual patching with a hex editor.
Common findings: Credentials in cleartext config files, weak encryption (ROT13, Base64, or weak keys), SQL connection strings with passwords, and insecure local storage.
Phase 4: Binary Analysis & Reverse Engineering
This is where thick client testing gets technical.
Identify protection mechanisms. Is the binary packed? Obfuscated? Does it have anti-debugging checks? Anti-tampering? Understanding protections helps you bypass them.
Analyze authentication logic. How does the app verify credentials locally? Can you patch the binary to always return “authentication successful”? Many apps have flawed offline authentication.
Find the secrets. Search for cryptographic keys, licensing mechanisms, hidden functionality, and backdoor credentials. Use string analysis, entropy analysis, and pattern matching.
Test integrity checks. Can you modify the binary without detection? Do updates verify signatures? Can you inject malicious code into the application?
Tools: IDA Pro, Ghidra, radare2, PE Explorer, CFF Explorer.
Phase 5: Privilege Escalation Testing
Many thick clients request or require elevated privileges. This creates privilege escalation risks.
Test the installation process. Does the installer run with admin rights? Can you hijack DLL loading during installation? Are there race conditions?
Analyze update mechanisms. How does the app download and install updates? Can you perform man-in-the-middle attacks to install malicious updates? Are the update packages signed and verified?
Check for unsafe file operations. Does the app create files with overly permissive ACLs? Can you perform symbolic link attacks? DLL hijacking?
Test service interactions. If the app installs Windows services, test for unquoted service paths, weak service permissions, and arbitrary write vulnerabilities.
Common findings: Unquoted service paths, DLL hijacking opportunities, insecure update mechanisms, and weak file permissions on sensitive data.
Phase 6: Database & Backend Testing
Don’t forget about server-side security.
Test database connections. Are connection strings hardcoded? Can you extract database credentials from the binary or memory? Does the app use least-privilege database accounts?
SQL injection testing. Even thick clients can be vulnerable to SQL injection if they construct dynamic queries. Test all input fields and parameters.
Backend API testing. Standard web application testing applies to any backend services. Test for authentication bypass, broken authorization, injection attacks, and business logic flaws.
Common Thick Client Vulnerabilities to Look For
Based on thousands of thick client penetration tests, here are the most common vulnerabilities:
1. Hardcoded Credentials (CWE-798)
Credentials embedded directly in the binary. Database passwords, API keys, encryption keys – all sitting in plaintext or weakly obfuscated in the executable.
How to find: Use the strings command, decompile the binary, search for common patterns (password=, key=, connectionString=).
Impact: Complete compromise of backend systems, data breaches, and lateral movement.
2. Insecure Local Storage (CWE-312, 922)
Sensitive data is stored locally without encryption. Configuration files, cached credentials, application data – all readable by anyone with file system access.
How to find: Monitor file operations with Process Monitor, check AppData and ProgramData directories, search for .config, .xml, .ini files.
Impact: Credential theft, data exposure, privilege escalation.
3. Weak Cryptography (CWE-327)
Using outdated algorithms (DES, MD5), weak key lengths, or implementing custom crypto (which is almost always broken).
How to find: Static analysis for crypto API calls, analyze encryption implementations, and test for known weak algorithms.
Impact: Encrypted data becomes readable, credentials compromised, sensitive information exposed.
4. Insufficient Certificate Validation (CWE-295)
Applications that don’t properly validate TLS certificates, allowing man-in-the-middle attacks.
How to find: Use an intercepting proxy with a self-signed certificate. If the app connects without warning, validation is broken.
Impact: Man-in-the-middle attacks, credential interception, data manipulation.
5. DLL Hijacking (CWE-427)
Applications that load DLLs from insecure locations, allowing attackers to inject malicious code.
How to find: Use Process Monitor to track DLL loading, check for missing DLLs in the search path, and test in directories with write access.
Impact: Code execution, privilege escalation, persistence.
6. Memory Corruption (CWE-119, 120)
Buffer overflows, use-after-free, and other memory safety issues in native code applications.
How to find: Fuzzing, static analysis tools, reviewing memory allocation/deallocation patterns.
Impact: Code execution, denial of service, complete system compromise.
7. Broken Access Control (CWE-284)
Authorization checks are implemented only in the UI or can be easily bypassed through direct function calls.
How to find: Use debuggers to call functions directly, modify memory to change user roles, and bypass UI restrictions.
Impact: Privilege escalation, unauthorized access to functionality and data.
Tools for Thick Client Penetration Testing
Your toolkit needs to cover multiple attack vectors:
Network Analysis:
- Wireshark – Traffic capture and protocol analysis
- Burp Suite – HTTP/HTTPS interception and testing
- Echo Mirage – Generic protocol interception
Reverse Engineering:
- IDA Pro / Ghidra – Disassemblers and decompilers
- dnSpy – .NET assembly browser and debugger
- JD-GUI – Java decompiler
Dynamic Analysis:
- x64dbg / WinDbg – Windows debuggers
- Process Monitor – File, registry, and process monitoring
- Process Hacker – Memory analysis and manipulation
Binary Analysis:
- Detect It Easy – Identify packers and protectors
- PEiD – Packer/compiler detection
- Dependency Walker – Analyze DLL dependencies
Specialized Tools:
- CFF Explorer – PE file analysis and editing
- Frida – Dynamic instrumentation framework
- API Monitor – Track API calls
Thick Client Penetration Testing Checklist
Here’s your systematic checklist for comprehensive thick client penetration testing:
Pre-Assessment:
- Identify application architecture (2-tier vs 3-tier)
- Determine technology stack
- Map network communications
- Identify local storage locations
- Document authentication mechanisms
Network Testing:
- Intercept and analyze all traffic
- Test TLS certificate validation
- Test for man-in-the-middle vulnerabilities
- Analyze API security
- Check for cleartext sensitive data
Binary Analysis:
- Decompile/disassemble the application
- Search for hardcoded credentials
- Identify cryptographic implementations
- Check for weak encryption
- Analyze authentication logic
Local Storage:
- Review configuration files
- Check registry entries
- Analyze temporary files
- Test file permissions
- Look for cached credentials
Memory Analysis:
- Dump and analyze process memory
- Search for sensitive data in RAM
- Test for cleartext passwords
- Check encryption key storage
Privilege Escalation:
- Test installation security
- Analyze update mechanisms
- Check for DLL hijacking
- Review service configurations
- Test file operation security
Database Testing:
- Extract connection strings
- Test for SQL injection
- Verify least privilege
- Check credential storage
When to Perform Thick Client Penetration Testing
Before production deployment. Security issues in thick clients are expensive to fix after distribution. Finding vulnerabilities during development saves money and reputation.
After major updates. New features mean new attack surface. Security testing should be part of your release process.
Annual security assessments. Threats evolve. New attack techniques emerge. Regular testing ensures ongoing security.
Compliance requirements. Many regulations (PCI DSS, HIPAA, SOC 2) require regular security assessments. Thick client testing should be part of your compliance program.
After security incidents. If your thick client was involved in a breach, comprehensive testing helps identify all vulnerabilities.
The DASVS Framework for Thick Client Penetration Testing
The Desktop Application Security Verification Standard (DASVS) provides a comprehensive framework for thick client security testing. It covers 12 critical security domains with over 150 specific, testable requirements:
- V1: Architecture and Design – Get the foundation right from the start
- V2: Authentication – Make sure users are who they say they are
- V3: Access Control – Control what authenticated users can actually do
- V4: Data Protection – Keep sensitive information safe
- V5: Communication – Secure network traffic
- V6: Validation and Output Encoding – Handle untrusted input without getting burned
- V7: File Operations – Manage file system access securely
- V8: Hardware Integration – Deal with USB devices and other peripherals
- V9: Logging and Monitoring – Know when something’s going wrong
- V10: Installation and Updates – Secure the distribution process
- V11: Self-Protection – Make your application harder to tamper with
- V12: UI Security and User Privacy – Protect the interface layer
Each domain includes specific requirements mapped to verification levels (L1 baseline, L2 enhanced, L3 high-risk) and Common Weakness Enumeration (CWE) identifiers.
Building Secure Thick Clients
Penetration testing finds vulnerabilities, but prevention is better than remediation.
Implement security from day one. Security isn’t a feature you add later. It’s an architectural requirement. Design with threat models. Build with secure coding practices. Test security throughout development.
Use platform security features. Operating systems provide security mechanisms – use them. Keychain/Credential Manager for secrets, code signing for integrity, sandboxing for isolation.
Assume breach mentality. Build applications that remain secure even when attackers have local access. Defense in depth. Multiple layers of security. No single point of failure.
Keep dependencies updated. Those third-party libraries? They have vulnerabilities. Track your dependencies. Apply security patches. Monitor for new CVEs.
Start Penetration Testing Your Thick Clients Properly
Thick client applications handle critical business operations and sensitive data. They deserve the same security attention as your web applications – actually, they need more.
Standard web application penetration testing misses most thick client vulnerabilities. You need specialized knowledge, tools, and methodology.
The complete Desktop Application Security Verification Standard (DASVS) provides the comprehensive framework you need for thick client security – whether you’re conducting penetration tests, building secure applications, or evaluating vendor software.
Ready to properly assess your thick client security? To see full DASVS framework with detailed testing requirements, common vulnerability patterns, and platform-specific guidance for Windows, macOS, and Linux applications go here: https://github.com/afine-com/DASVS
Don’t let your thick clients be the weak link in your security posture.