Critical Infrastructure
Penetration Testing
Infrastructure penetration testing for organizations where operational disruption carries safety and regulatory consequences. Decade of experience in SCADA, OT networks, and industrial control systems.
Infrastructure Penetration Testing That Reduces Risk
Here's what happens with most annual penetration tests:
Testing that doesn't account for OT operational constraints
Findings your operations team struggles to prioritize
Surface-level scans that miss critical attack paths
We show you what breaks, how it breaks, and what customer data is exposed
Through infrastructure penetration testing we find where security mistakes have operational consequences. You see which attack paths work, what to fix and why.
Why Organizations Choose AFINE for Infrastructure Penetration Testing
We've spent 10 years conducting infrastructure penetration testing across critical operations. You get researchers who know what breaks in SCADA environments and reports that show exactly how we exploited your systems. Each finding includes working proof-of-concept and operational impact.

Our Services
Our Critical Infrastructure Penetration Testing Services
SCADA Systems Testing
We test SCADA protocol implementations, HMI authentication, and network segmentation. This includes historian database security, engineering workstation access, and vendor remote access channels.

Industrial Control Systems (ICS)
We analyze PLC logic and controller communications for unauthorized modification risks. Testing covers safety system bypasses, process manipulation attacks, and whether monitoring systems detect malicious changes.

OT Infrastructure Penetration Testing
We test network boundaries between IT and OT environments, verify firewall rules, and simulate attack paths from corporate networks into control systems. Testing includes industrial protocol manipulation and encryption verification.

Web Applications Testing
We test SCADA web interfaces, energy management portals, and HMI web applications. This includes authentication bypasses, injection attacks, and vulnerabilities specific to real-time monitoring dashboards and control interfaces.

Cloud Infrastructure
We assess cloud-connected SCADA systems, IaaS/PaaS hosting industrial applications, and hybrid cloud-OT architectures. Testing covers API security, identity management, and whether cloud misconfigurations expose control systems.

Mobile Applications
We test field operator apps, remote monitoring applications, and mobile SCADA clients. This includes authentication security, data storage vulnerabilities, and whether mobile access creates unauthorized entry points to control systems.

Social Engineering
We conduct targeted attacks against operations staff - phishing control room operators, phone-based attacks on maintenance teams, and physical access attempts. Tests verify whether your teams recognize operational security threats.

Embedded Devices & Firmware
We analyze industrial controller firmware, RTU devices, and protocol gateways. Testing covers backdoors, unauthorized code, and protocol vulnerabilities that persist through software updates.

AI/ML Systems Security
We test AI model security, prompt injection attacks, and training data poisoning. This includes API authentication, model inference manipulation, and whether AI decision-making can be compromised to cause operational disruptions.

The Enterprise Security Software We Hacked
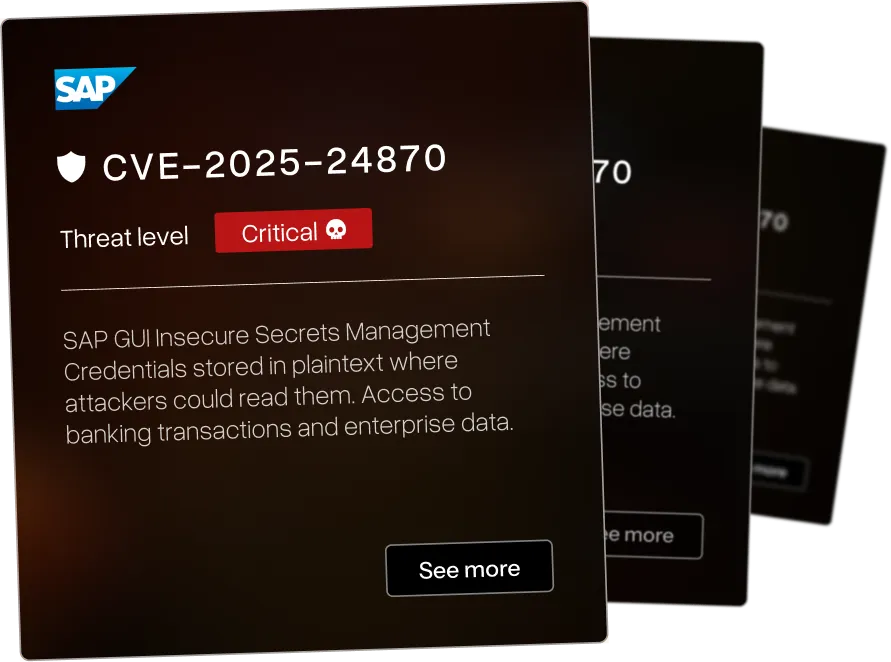
Our infrastructure penetration testing discovers vulnerabilities in the platforms critical infrastructure organizations depend on. We exploit both known CVEs and the vulnerabilities nobody's documented yet.


Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code






Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts




View All CVEs We've Published
.webp)


.webp)
The AFINE Adaptive Security Framework (AASF)
A framework developed from a decade of security assessments and continuously refined as attack methods evolve. Our methodology reflects current threat patterns and the practical security decisions organizations face as their attack surface expands.
We’re ready to deliver next-level security
Why Organizations Trust Us
Infrastructure Penetration Testing FAQ
Let's Discuss Your Security Posture
Critical infrastructure requires specialized security testing. Schedule an assessment to discuss your environment, regulatory requirements, and operational constraints.