Red Team Exercise
for Critical Infrastructure
Red Team Exercise by Security Researchers With 150+ CVEs in SAP, IBM, Microsoft, CyberArk and more...
Red Team Excersise Validating Your Defenses
Here's what happens with most security programs:
Controls look good on paper.
Your SOC has detection rules.
Network segmentation between IT and OT is documented.
Everyone assumes the defenses work.
We show you what breaks, how it breaks, and what customer data is exposed
We validate your defenses through adversary simulation. You see which attack paths reach critical systems, which controls failed during exploitation, and get remediation priorities based on risk in your environment
Why Organizations Choose AFINE Red Team Exercises
We've conducted red team exercises on industrial systems for 10 years. You get operators who understand adversary movement from contractor networks to control infrastructure, and reports showing which controls failed. We simulate realistic attack chains to SCADA systems.

Purple Team Mode Available
Most critical infrastructure clients choose purple team collaboration during red team exercise. Your SOC sees our activity in real time. We explain what we're doing, what it looks like in logs, and how detection should work for OT-targeted attacks.
You get both security validation and immediate SOC improvements. Your analysts learn what sophisticated attacks on industrial systems look like while they're happening - from IT-to-OT lateral movement to control system compromise attempts.
Our Services
Attack Path Validation to Control Systems
We simulate adversary movement from initial compromise to control system access during red team exercises. This includes privilege escalation routes, credential theft from engineering workstations, and lateral movement through IT/OT boundaries. Testing validates whether your defenses stop attackers before they reach operational technology.

SOC Detection and Response
We test if your SOC detects sophisticated attacks on industrial systems through red team exercises. SIEM rules for IT-to-OT lateral movement. Credential dumping from engineering environments. Alert triggering and response times. Purple team mode provides real-time feedback on detection capabilities for OT-targeted attacks.

IT/OT Segmentation Effectiveness
We simulate attacks from corporate networks to operational technology environments during red team exercises. This includes firewall bypass attempts, network boundary testing, and whether segmentation rules actually stop lateral movement to SCADA systems and control infrastructure.

Third-Party and Vendor Access
We assess vendor integration security and remote access paths through adversary simulation. This includes contractor VPN exploitation, partner connection compromise, and whether third-party access provides routes to control systems. Testing validates monitoring coverage for external connections.

Physical Security and Social Engineering
We test physical access controls and employee manipulation during red team exercises. This includes building penetration to control rooms, credential harvesting through social engineering, and tailgating scenarios. Testing validates whether physical security breaches translate to control system access.

Insider Threat Simulation
We simulate what happens when legitimate access gets abused during red team exercises. This includes privileged account compromise, data exfiltration from authorized systems, and malicious activity from trusted accounts. Testing if your monitoring catches insider threats that look like normal operational behavior.

Multi-Vector Attack Scenarios
We combine digital attacks, social engineering, and physical penetration during red team exercises. This includes phishing campaigns targeting operators, exploitation of internet-facing systems, and coordinated attacks across multiple entry points. Testing validates your organization's ability to detect and respond to complex threats.

Command and Control Detection
We test whether your defenses detect command and control infrastructure during red team exercises. This includes C2 communication to compromised systems, data exfiltration channels, and persistence mechanisms. Testing validates if your SOC identifies ongoing attacker presence in industrial environments.

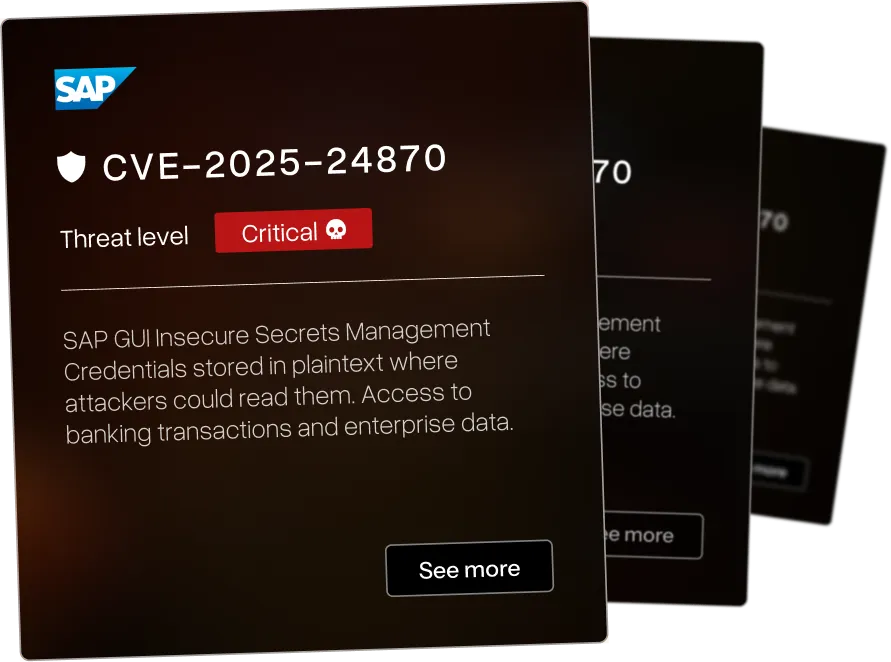
The Enterprise Security Software We Hacked
Our red team exercise validates defenses across enterprise platforms running critical operations. We simulate sophisticated adversaries exploiting both known CVEs and zero-days that nobody's documented yet.


Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code






Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts




View All CVEs We've Published
.webp)


.webp)
The AFINE Adaptive Security Framework (AASF)
A framework developed from a decade of security assessments and continuously refined as attack methods evolve. Our methodology reflects current threat patterns and the practical security decisions organizations face as their attack surface expands.
We’re ready to deliver next-level security
Why Organizations Trust Us
Red Team Exercise FAQ
Let's Discuss Your Security Posture
We scope every red team exercise based on your infrastructure and threat landscape. Book an assessment below to discuss your requirements.