Red Team Security Testing
for Fintech
Red Team Security Testing for Fintech by Security Researchers With 150+ CVEs in SAP, IBM, Microsoft, CyberArk and more...
Red Team Security Testing Your Defenses
Most security programs follow this pattern:
Controls look good on paper.
Your SOC has detection rules.
Network segmentation between IT and OT is documented.
Everyone assumes the defenses work.
We show you what breaks, how it breaks, and what customer data is exposed
We simulate attackers who've breached your perimeter and test if they can reach payment processing infrastructure, manipulate transactions, or access customer funds. You see which attack paths work and if your defenses stop them.
Why Fintech Companies Choose AFINE for Red Team Security Testing
We've conducted red team security testing on fintech companies and payment platforms in production for 10 years. You get operators who know how adversaries move from initial compromise to payment processing systems, and reports showing exactly which controls failed. From assumed breach positions, we test lateral movement to transaction engines and customer data infrastructure.

Purple Team Mode Available
Most fintech clients choose purple team collaboration during red team security testing. Your SOC sees our activity in real time. We explain what we're doing, what it looks like in logs and how detection should work.
You get both security validation and immediate SOC improvements. Your analysts learn what sophisticated attacks look like while they're happening.
Our Services
What We Cover in Red Team Security Testing for Fintech
Payment Processing Infrastructure
We test lateral movement from internet-facing systems to payment engines during red team security testing. Cloud workload isolation effectiveness. Privilege escalation routes. API authentication controls. We map attack paths from compromised containers to transaction systems and customer data stores.

Payment Rails and Third-Party Integrations
We test attack paths to Stripe, Plaid, and payment processor connections. Webhook manipulation and replay attacks. OAuth flow exploitation. Testing if your SOC detects unauthorized access to payment gateway integrations before fund movement.

Mobile and Web Applications
We simulate account takeover and session hijacking attacks. API abuse bypassing rate limits and authorization. Transaction manipulation through race conditions. Testing if fraud detection stops sophisticated attacks on customer authentication and payment flows.

Admin Panels and Internal Tools
We test access paths to privileged dashboards, customer support tools, and operational systems. Testing if compromising these panels leads to unauthorized fund transfer capability or customer data access.

SOC Detection and Response
We test if your SOC detects sophisticated attacks on fintech infrastructure through red team security testing. Do SIEM rules fire on lateral movement to payment systems? Does EDR catch credential access? Purple team mode provides real-time feedback on detection capabilities.

Third-Party Integration Security
We assess payment processor, banking API, and identity provider integration points. Authorization across external connections. Whether compromise at one integration provides access to customer funds and whether monitoring covers third-party activity.

Insider Threat Simulation
We test what happens when legitimate access gets abused - developer accounts compromised, production data exfiltrated from CI/CD pipelines, malicious activity from authenticated APIs. Testing if your monitoring catches insider threats that look like normal deployment activity.

AI/ML Security Testing
We test AI systems fintech companies deploy - prompt injection on customer service chatbots, fraud detection model manipulation, recommendation system poisoning. Data extraction from model outputs. Testing if guardrails prevent unauthorized access to customer data or manipulation of transaction scoring.

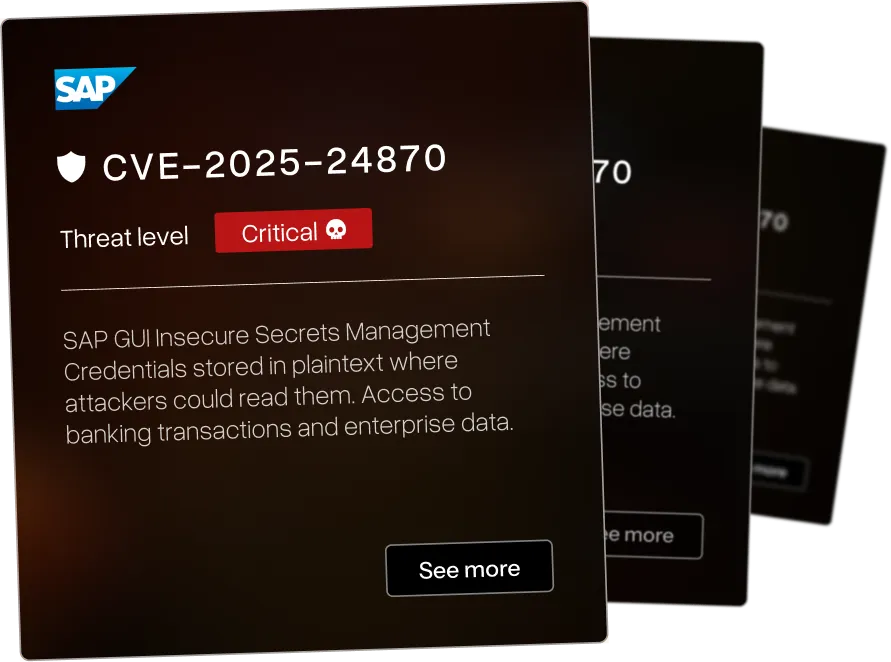
The Enterprise Security Software We Hacked
Our red team security testing operators discover vulnerabilities in the platforms financial technology companies depend on. We exploit both known CVEs and the vulnerabilities nobody's documented yet.


Memory corruption in Microsoft Edge (EdgeHTML) allows remote code execution via crafted web content




.webp)

Remote code execution via insecure deserialization in IBM i Access Client Solutions allows attackers to execute arbitrary code






Missing rate limiting on password change in CyberArk EPM allows brute-force attacks against user accounts




View All CVEs We've Published
.webp)


.webp)
The AFINE Adaptive Security Framework (AASF)
A framework developed from a decade of security assessments and continuously refined as attack methods evolve. Our methodology reflects current threat patterns and the practical security decisions organizations face as their attack surface expands.
We’re ready to deliver next-level security
Why Organizations Trust Us
Red Team Security Testing FAQ
Let's Discuss Your Security Posture
We scope every red team exercise based on your infrastructure and threat landscape. Book an assessment below to discuss your requirements.