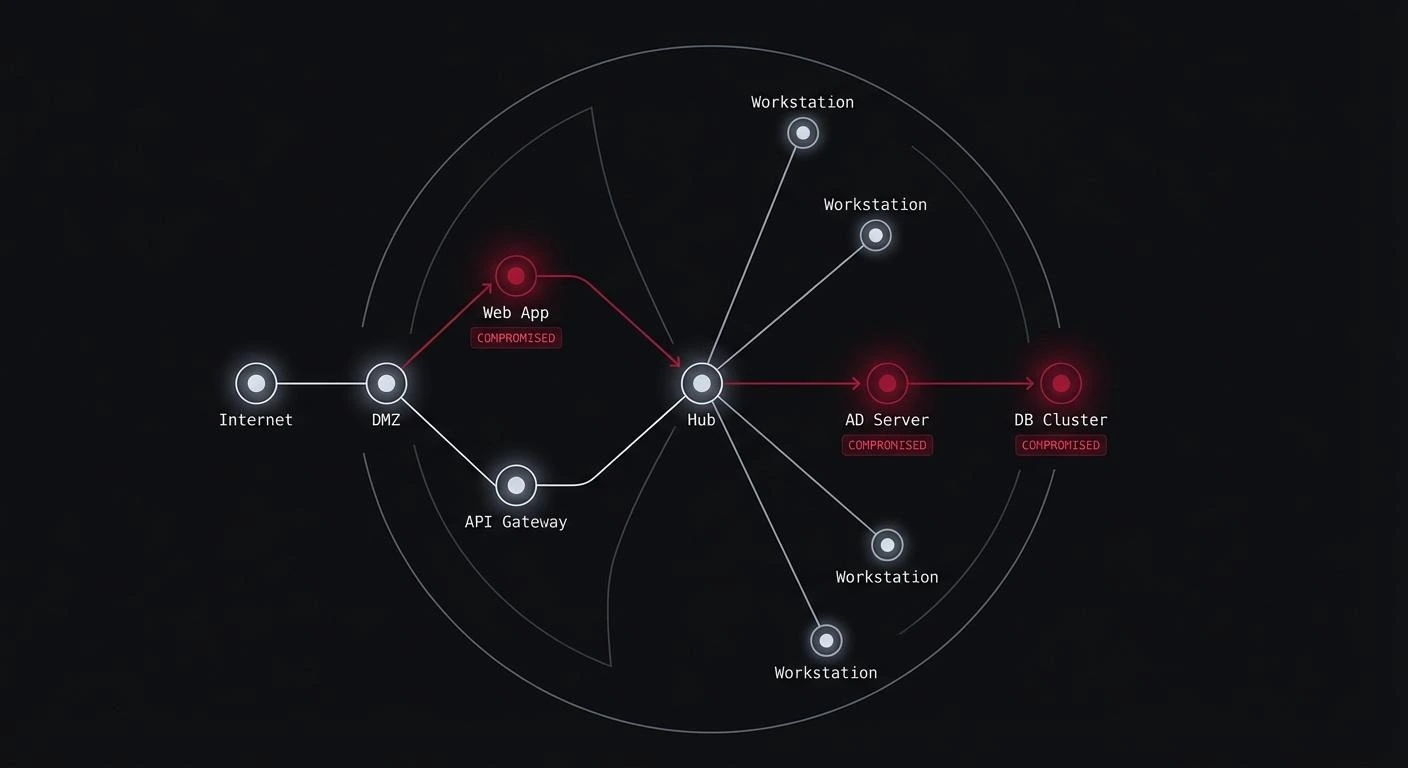
Desktop applications handle critical business operations across enterprises. Banking software processes transactions. Healthcare apps store patient records. Manufacturing tools control production systems. They all share common security challenges that standard desktop application testing approaches miss.
The problem is straightforward: most security testing methodologies were built for web and mobile applications. They don’t account for direct file system access, local credential storage, or applications running with elevated privileges on systems that haven’t seen security patches in years.
Why Desktop Application Testing Falls Through the Cracks
Most security frameworks focus on web or mobile platforms. Web applications have OWASP ASVS. Mobile applications have MASVS. Desktop applications? There wasn’t a comprehensive standard until recently.
This gap exists because desktop security presents challenges that web and mobile frameworks don’t address.
Desktop applications run with broad system access. There’s no browser sandbox. No mobile OS capability restrictions. Without proper controls, applications can access files across the entire system, manipulate registry entries, and interact directly with hardware.
Applications need to run on systems outside organizational control. Is that machine running an outdated operating system without recent security patches? The application still needs to work there. Security inherits all the weaknesses of the underlying platform.
Physical access fundamentally changes the threat model. Someone with machine access can attach debuggers to running processes, modify memory in real time, patch executables, and reverse-engineer the codebase. These threats rarely apply to web applications, where code executes on controlled servers.
What Makes Desktop Application Testing Different?
Testing desktop application security requires different approaches than testing web applications. The attack surface differs in fundamental ways.
Local execution means direct access to everything. Configuration files are readable. Process memory can be dumped. Binaries can be modified. Local storage sits unprotected. Each file the application touches becomes a potential target.
Multiple communication layers require testing. Applications connect to databases directly, use inter-process communication with other local processes, read and write files across the system, and potentially interact with hardware. Each communication channel has distinct security requirements.
Client-side logic operates in hostile environments. Everything running on user machines is under their control. License checks can be patched. Authentication logic can be modified. Encryption keys can be extracted from memory. Security models must account for completely untrusted client environments.
The 12 Desktop Application Testing Critical Areas
Based on the newly released Desktop Application Security Verification Standard (DASVS), here’s what actually matters when testing desktop app security:
1. Architecture & Design: Get the Desktop Application Foundation Right
Most security problems stem from architectural decisions made before a single line of code was written.
Test whether your app follows least privilege principles. Does it request only the minimum OS permissions needed? Does privilege elevation happen only when necessary, with proper user notification?
Check if security-sensitive operations require additional verification beyond initial authentication. Your architecture documentation should clearly show trust boundaries and data flows.
Quick test: Can you explain where sensitive data flows through your application and which components have elevated privileges? If not, your architecture needs work.
2. Authentication: Local is Different
Desktop apps can’t always phone home to verify credentials. You need authentication that works offline without compromising security.
Never store credentials in cleartext. Use platform-approved storage (Keychain on macOS, Credential Manager on Windows, Secret Service on Linux). Password policies should include minimum length and complexity requirements, with checks against known breach databases.
Implement rate limiting for authentication attempts, even in offline scenarios. After repeated failures, introduce delays or temporary lockouts.
Quick test: Search your codebase for password-related strings. If you find plaintext credentials or hardcoded secrets, you’ve got immediate problems.
3. Access Control: UI Locks Aren’t Enough
Here’s where most developers mess up: they secure the UI and think they’re done.
Authorization checks need to happen in your business logic, not just in UI components. What happens if someone calls your admin function directly, bypassing the disabled button? What if another process invokes it through IPC?
Test whether access control rules work on a trusted enforcement layer that can’t be bypassed. Verify that file operations properly respect user permissions. Check that admin functions are genuinely separated from normal user operations.
Quick test: Can you call privileged functions directly without going through the UI? If yes, your access control is broken.
4. Data Protection: Everything Local Needs Encryption
Your app stores configuration files, cached data, user content, and potentially credentials. All locally. All are vulnerable if not properly encrypted.
Use platform-approved encryption APIs. AES-256 minimum. Keys should never be hardcoded in your binary. Use OS-provided key storage where available (TPM, Secure Enclave, etc.).
Don’t forget memory. Sensitive data should be cleared from RAM when no longer needed. Memory dumps shouldn’t expose secrets.
Quick test: Copy your application’s data folder. Can you read sensitive information without decryption? If so, your data protection isn’t working.
5. Communication: Trust No Network
Whether talking to remote servers or other local processes, communication channels need protection.
All network traffic should use TLS with proper certificate validation. No self-signed certs in production. Implement certificate pinning for critical connections.
Inter-process communication needs authentication and integrity checks. Don’t trust data from other processes just because they’re running on the same machine.
Quick test: Run a proxy to inspect your network traffic. If you see sensitive data in cleartext or your app accepts invalid certificates, you’ve got problems.
6. Input Validation: Sanitize Everything
Desktop apps accept input from files, network sources, IPC channels, and user interfaces. Every input source is a potential attack vector.
Validate all inputs against defined schemas. Use positive validation (allow-listing) rather than blocking known bad inputs. User-supplied file paths must be sanitized to prevent path traversal attacks.
Never use dangerous functions like eval() or execute user-controlled data as code. OS command execution should never include unsanitized user input.
Quick test: Try opening a maliciously crafted file or passing unexpected data through your app. Does it crash, expose errors, or behave unexpectedly?
7. File Operations: Handle With Care
Files are where desktop apps differ most from web apps. You’re reading and writing across the file system, often with elevated privileges.
Verify that file operations happen with the minimum necessary privileges. Files created by your app should have proper permissions restricting access to authorized users only. Validate file types, sizes, and contents before processing.
For file formats that may contain malicious payloads (PDF, XML, ZIP), use secure parsers configured to prevent attacks such as XXE injection and zip bombs.
Quick test: Check the permissions on files your app creates. Can other users read sensitive data they shouldn’t access?
8. Hardware Integration: Don’t Trust Devices
USB drives, printers, cameras, and biometric readers. Each device connection is an attack opportunity.
Implement access controls for hardware resources. Validate and authenticate devices before establishing trusted communication. Data exchanged with external devices needs validation for integrity.
Keep device drivers and libraries updated. Minimize the attack surface exposed to potentially malicious devices.
Quick test: What happens when you connect an unexpected device or send malformed data from a peripheral? Does your app handle it gracefully?
9. Logging & Monitoring: Know What’s Happening
You need logs for incident detection and forensics, but desktop logging is tricky. Balance visibility with privacy and performance.
Log security-relevant events: authentication attempts, privilege changes, access control failures. Include enough information for analysis without capturing sensitive data or PII.
Protect logs from tampering. Implement log rotation to prevent disk exhaustion. Encrypt logs containing sensitive information.
Quick test: Review your log files. Do they contain passwords, personal data, or other sensitive information that they shouldn’t?
10. Installation & Updates: Secure the Supply Chain
If attackers compromise your installer or update mechanism, they can distribute malware to every user.
Installation packages must be digitally signed and verified before execution. Updates should download over HTTPS with certificate validation and signature verification before installation.
The update mechanism itself can’t become an attack vector. Verify that updates maintain secure configurations and don’t reset security settings.
Quick test: Intercept an update check. Can you trick your app into installing a malicious update?
11. Self-Protection: Resist Tampering
Attackers with local access can attach debuggers, modify memory, and patch your executable. You won’t stop determined attackers, but you can make it harder and detect tampering attempts.
Implement runtime integrity checks for critical code and data. Detect debugging attempts when handling sensitive operations. Use checksums or signatures to verify component integrity.
Leverage platform security features like ASLR, DEP, and Control Flow Guard. Never hardcode secrets in your binary.
Quick test: Attach a debugger to your running app. Can you easily modify behavior or extract secrets?
12. UI Security: Stop Data Leakage
The UI is where sensitive data leaks if you’re not careful.
Mask sensitive information like passwords in UI components. Prevent or obscure screenshots when displaying sensitive data. Control copy-paste operations for fields containing secrets.
Don’t expose sensitive information in window titles, error messages, or notifications that might appear in screen sharing or over-the-shoulder viewing.
Quick test: Take a screenshot while your app displays sensitive data. What information is visible? Share your screen during a video call. What can others see?
Your Next Steps in Desktop Application Testing
Desktop application security isn’t optional anymore. With desktop apps handling everything from financial records to healthcare data, the security bar needs to rise.
Start by identifying which verification level matches your risk profile:
- Level 1 (Baseline): Every desktop app should meet these requirements. They protect against common, well-known attacks.
- Level 2 (Enhanced): For apps handling sensitive business data. More sophisticated controls and thorough development process integration.
- Level 3 (High-Risk): Mission-critical applications where breach would be catastrophic. Assumes skilled attackers will specifically target your app.
The complete Desktop Application Security Verification Standard (DASVS) provides detailed, testable requirements across all 12 domains. It’s the first comprehensive security standard built specifically for desktop threats.
Whether you’re writing code, conducting security assessments, or evaluating vendor software, DASVS gives you a systematic framework for building and verifying secure desktop applications.
Ready to secure your desktop app properly? Get the full DASVS framework for free, with detailed verification requirements, implementation guidance, and platform-specific recommendations.