In “When Memory Refuses to Forget: Sensitive Data Persistence in Desktop Application“, I explored the threat of sensitive data lingering in memory, showing that software often fails to erase secrets securely after use. Today, I’ll demonstrate how credential harvesting through this vulnerability played a pivotal role in a real-world red team engagement involving CVE I found last year in Check Point’s SmartConsole (R81.20).
Enjoy!
Credential Harvesting via CVE-2024-24915: Proof of Concept
The vulnerability lies in the fact that credentials are not cleared from memory after being used. To reproduce:
- Sign in to the application:
- Create a memory dump:
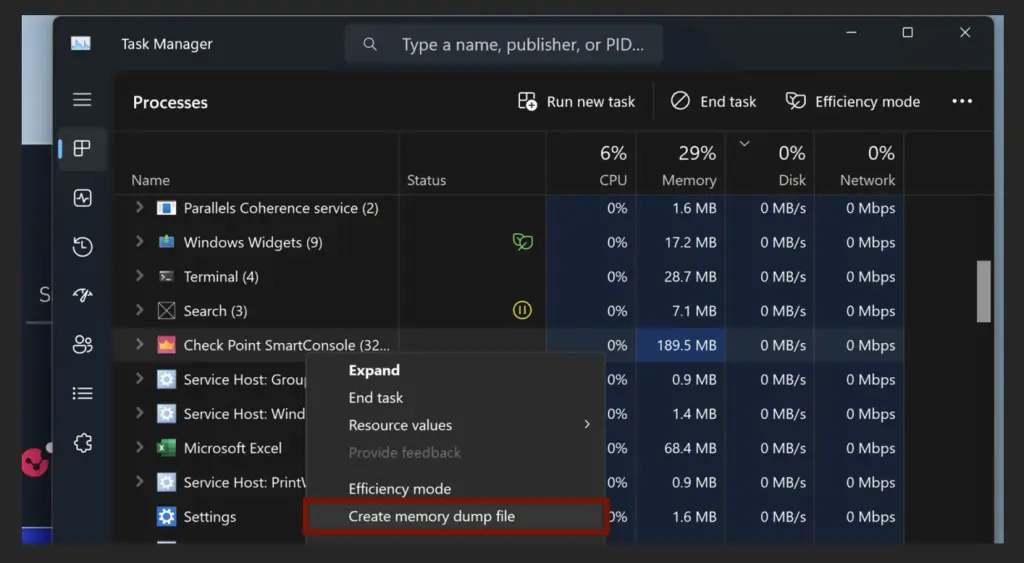
- Search for strings used for signing:
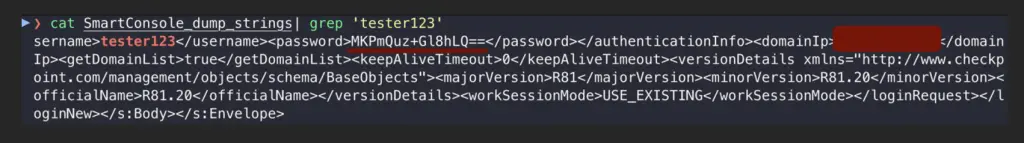
Okay, but how can adversaries use that? Is this a real threat? Let’s find out!
Red Team Context
The story starts with a successful spear-phishing campaign. I used a vulnerable SmartConsole installer on a company-wide SMB share. The initial access vector utilized DLL hijacking, by planting a malicious profapi.dll alongside the installer (as detailed in my earlier post DLL Hijacking in Check Point SmartConsole installer aka CVE-2024-24916). Once a user ran the installer, it triggered a reverse shell.
After establishing a persistance, the second vulnerability I found CVE-2024-24915, comes into play.
Exploiting Plaintext Credentials: Credential Harvesting in Process Memory
Here’s where insecure memory handling in SmartConsole became a gold mine. In each shell session, I began dumping the process memory of SmartConsole to harvest user credentials. Thanks to CVE-2024-24915, these credentials are left in cleartext within the process memory.
It is an example of how the Issue from When Memory Refuses to Forget: Sensitive Data Persistence in Desktop Application is a real threat, especially in a corporate environment.
Lateral Movement Through Credential Harvesting
This is significant for Lateral Movement as harvested plaintext credentials can be immediately abused for password reuse with automated tools like netexec to spray across services such as:
- Remote Desktop Protocol (RDP) for interactive access to user desktops or servers.
- Server Message Block (SMB) for file sharing and remote command execution.
- Windows Remote Management (WinRM) to execute remote PowerShell or management commands.
- Windows Management Instrumentation (WMI) for stealthy, remote code execution.
- LDAP queries to enumerate users, computers, and AD objects.
- Kerberos for Pass-the-Ticket or Pass-the-Hash attacks.
The risk extends beyond on-prem environments—those same credentials often grant access to:
- Cloud Services like Office 365, Google Workspace, Salesforce, AWS, Azure, and more.
- HTTP/Web Applications (internal and external), VPN portals, time-tracking tools, HR platforms, Jira, Confluence, and other business-critical resources.
The combination of DLL hijacking for initial compromise and plaintext credential harvesting in memory allows a red team – or an attacker – to chain these vulnerabilities with devastating effect. It is also a good moment to mention a timeless security advisory to NEVER USE THE SAME PASSWORD TWICE.
Final Words
The persistence of credentials in userland memory can turn a single successful phish into a domain-wide compromise. Modern red team engagements demonstrate that, all too often, memory-based credential harvesting remains a critical attack vector.