Microsoft Defender SmartScreen bypass with copy-paste from ISO

In recent years, attackers have constantly evolved methods to exploit vulnerabilities in widely used security systems. One such mechanism, Microsoft Defender SmartScreen, is crucial in protecting users from malicious files by identifying and flagging untrusted executables downloaded from the Internet. However, my recent finding reveals a concerning bypass that allows attackers to execute malicious code without triggering SmartScreen warnings when using ISO image files.
This article presents a detailed breakdown of how ISO files can be used to bypass Microsoft Defender SmartScreen protections. It demonstrates a Proof of Concept where an executable extracted from an ISO file can run without the typical SmartScreen alert. This bypass represents a significant concern, particularly in phishing attacks, where the attacker instructs the victim to download and run malware.
By the end of this article, you will clearly understand how this bypass works, the steps involved in replicating it, and the potential security implications for users. If you are interested in T1566 – Phishing techniques or want to learn basics, I recommend another article linked below as an introduction:
Enjoy reading!
Technical Details of the Attack Vector
Microsoft Defender SmartScreen is designed to protect users by warning them of potentially harmful files, especially executables downloaded from the internet. Typically, when a user attempts to run such a file, SmartScreen inspects it and displays a warning if it deems the file untrusted. This mechanism can be a strong deterrent against phishing attacks, as users are less likely to proceed if they are informed of a potential threat. Below, we may see an example of SmartScreen in action:
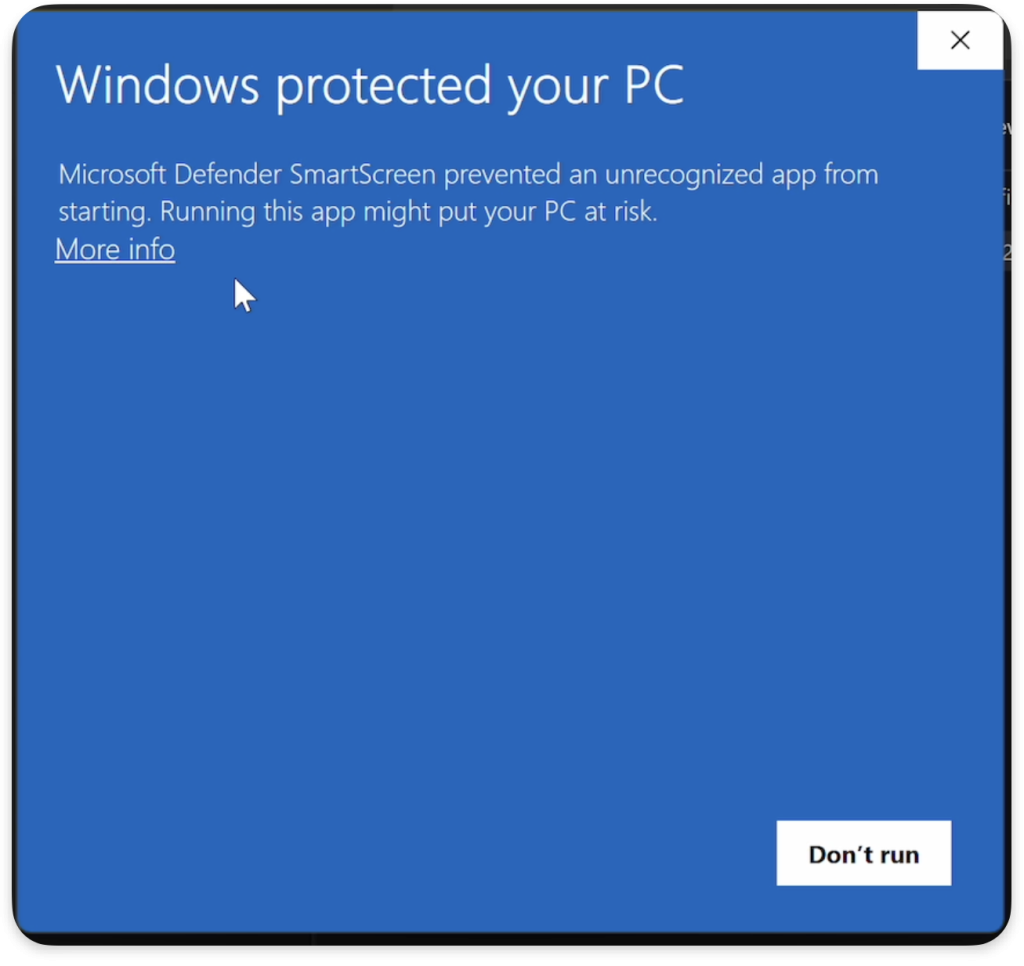
However, a critical oversight occurs when dealing with ISO files. When an executable is copied from an ISO image and pasted into the filesystem, it is not marked with the “Mark of the Web” (MOTW) attribute, which is essential for triggering SmartScreen warnings. As a result, the executable can be run without any intervention from Microsoft Defender SmartScreen, bypassing this crucial security feature.
The Attack Scenario
Here’s how a typical attack leveraging this bypass unfolds:
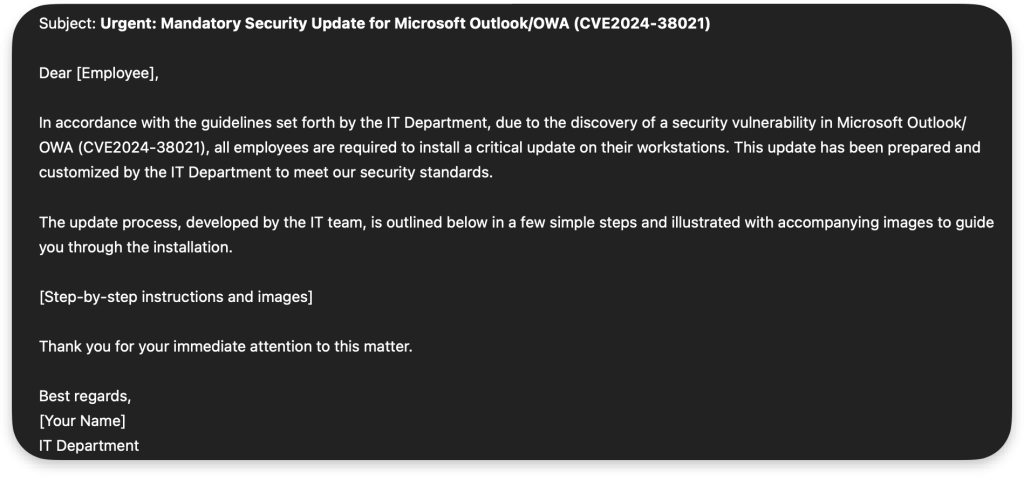
1. The phishing email: The attacker sends an email containing a link to download a malicious ISO file, along with instructions to move the executable from the ISO to the user’s Desktop to “make it work.”
For this step, the attacker may use some pretexting, depending on the previous reconnaissance of the targeted company. Below is a small all-around template commonly seen on the phishing assessments:
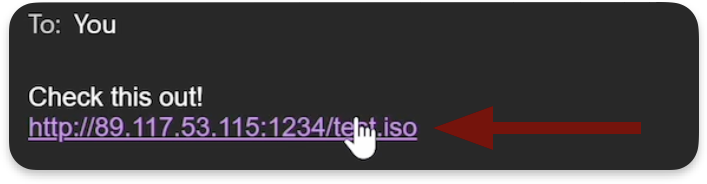
2. Downloading the ISO file: The victim clicks on the link and downloads the ISO file, which is hosted on a publicly accessible server.
3. Mounting the ISO file: The victim double-clicks on the ISO file to mount it. This action opens the contents of the ISO, which contains a malicious executable.
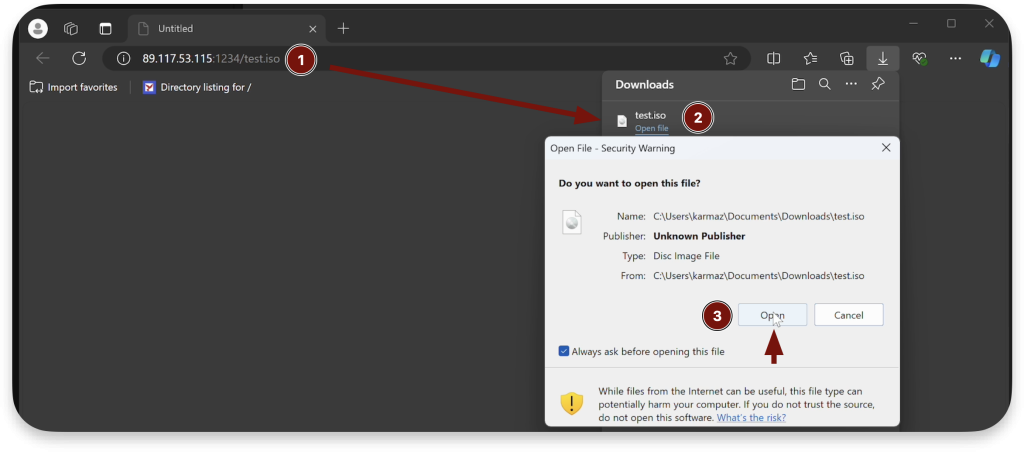
4. Moving the executable: The attacker instructs the victim to drag and drop the executable from the mounted ISO to the Desktop. Crucially, the executable does not inherit the MOTW at this stage, as it was transferred directly from a mounted ISO file.
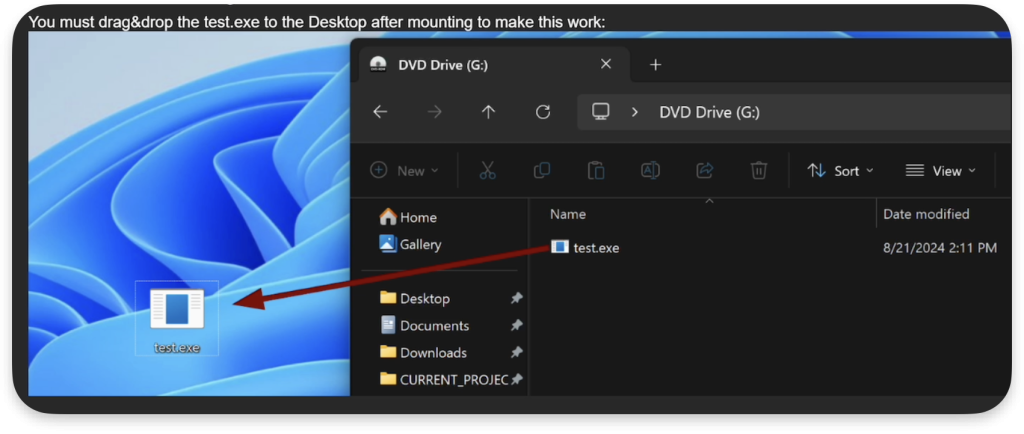
5. Running the executable: When the victim double-clicks on the executable on their Desktop, Microsoft Defender SmartScreen fails to intervene, allowing the malware to run undetected.
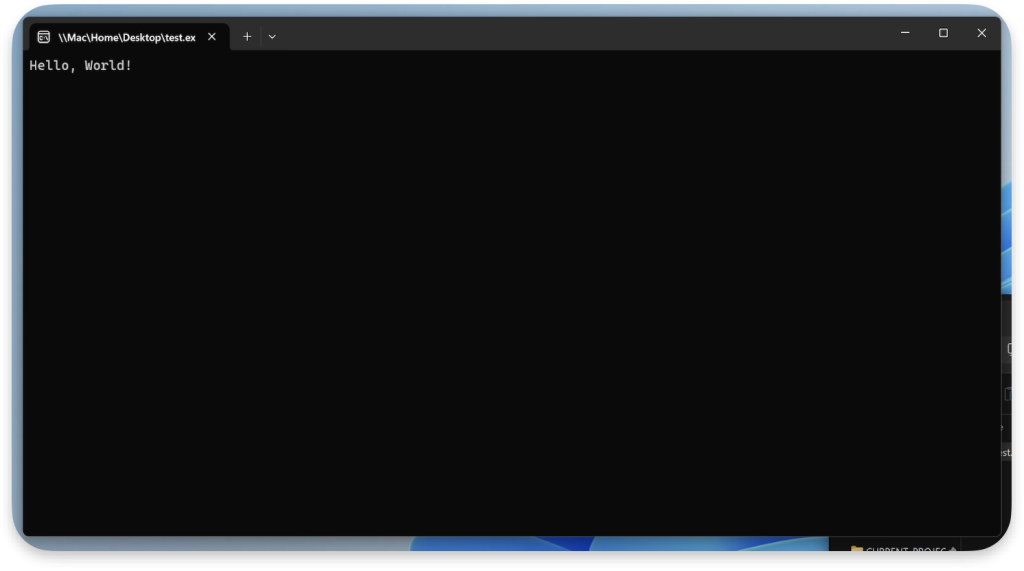
Proof of Concept
The PoC was recorded in the attached video below to observe the bypass in action:
To better understand this vulnerability, let’s walk through the process step by step:
1. Prepare the executable: Create a “malicious” executable. Remember that in a real scenario, the actual malware should be additionally obfuscated so it is not detected by EDR software.
2. Create an ISO file: Place the executable inside an ISO file. We can use a tool such as PackMyPayload for this purpose. It can be done with the following command, which generates ISO containing the EXE:
python3 PackMyPayload.py test.exe test.isoCode language: CSS (css)3. Host the ISO file: Use a publicly accessible server using, for instance, Python’s simple HTTP server. You can then share the link (e.g., http://123.123.123.123:80/test.iso) with the target victim.
python3 -m http.server 80Code language: CSS (css)4. Download and open the ISO: Use the mail message as the vector to instruct the victim to download the ISO using the provided link and double-click to mount the ISO.
5. Extract the executable: The victim drags and drops EXE from the mounted ISO to their Desktop.
6. Run the executable: The victim double-clicks on EXE on their Desktop. At this point, no SmartScreen warning appears, and the executable runs without hindrance.
7. Verify the control step: As a control, double-clicking on EXE directly within the mounted ISO should trigger a SmartScreen warning, as the MOTW is applied when the executable is run from within the ISO.
Security Implications
This SmartScreen bypass poses risks for users, especially in phishing attacks. Since executables extracted from ISO files are not marked with MOTW, users may unknowingly run malicious files without security warnings. Attackers can easily leverage this vulnerability to distribute malware via ISO files.
Conclusion & Mitigations
While Microsoft Defender offers a robust defense against many forms of malware, this ISO-based bypass presents an apparent vulnerability. Users should exercise caution when handling ISO files, especially those received through suspicious emails from untrusted sources. Security teams and users alike must be aware of this issue. Until a patch addresses this oversight, organizations must remain vigilant and educate users on the risks associated with executing files from ISO images.
Final words
I reported the issue to Microsoft through the MSRC Research Portal. They have closed it as a Low-risk issue, which I agreed on. There will be no CVE for that, and the issue will be patched later rather than sooner. Because of that, I thought it would be better to disclose it publicly rather than wait for the patch so the user can be aware of this issue from now on.
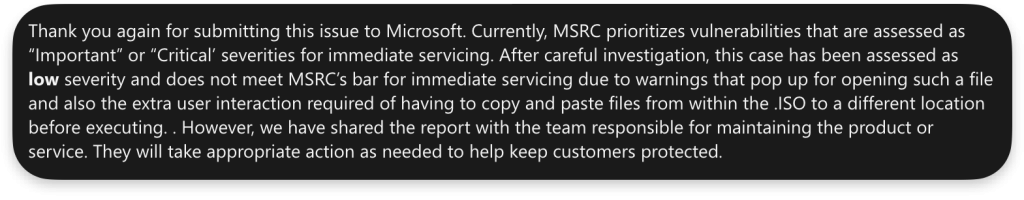
Microsoft agreed on that, which is why this blog post was published.
If this blog post interests you and you are interested in Cybersecurity in general, I encourage you to visit our AFINE blog regularly for new knowledge. I hope you like it!

